AdGuard pre iOS 4.5.10


Dátum vydania: 14. marca 2025
This is a technical update aimed to increase the app stability and fix minor bugs.
AdGuard pre iOS 4.5.9


Dátum vydania: 17. februára 2025
This is a technical update aimed to increase the app stability and fix minor bugs.
AdGuard pre iOS 4.5.8


Dátum vydania: 30. decembra 2024
This update is just a chill guy that makes the app up to 30x faster. We did some work on Safari Converter, so now AdGuard filtering rules are converted to Safari rules in just 0.5–2 seconds instead of 10–30. You will notice the difference especially when updating, enabling, or disabling filters and turning protection on.
Let's give a bit of explanation.
Updating and/or applying filters involves three steps: downloading new versions to the AdGuard app (a seamless process), converting AdGuard rules into Safari-compatible rules (now 30x faster thanks to optimization), and loading the rules into Safari. In the case of the last step, however, on iOS and iPadOS, the process takes 6–15 seconds per small content blocker to compile rules compared to fractions of a second on macOS. This delay affects user experience and slows filter updates, which are critical for ad blockers' performance. AdGuard has reported the issue to Apple (ticket ID: FB16130983) and hopes for a fix in 2025. You can read the blog post for more details.
AdGuard pre iOS 4.5.7


Dátum vydania: 29. októbra 2024
Right after the v4.5.6 release, we found that sharing YouTube videos to AdGuard’s internal ad-free browser was impossible on iOS 18. We fixed that, and now you can enjoy ad-free YouTube.
Changelog
Fixes
Opening YouTube videos in AdGuard’s internal ad-free browser doesn’t work on iOS 18 #2387
AdGuard pre iOS 4.5.6


Dátum vydania: 23. októbra 2024
This update brings a bit of style: iOS 18 introduced customizable app icons, so now they’re available for the AdGuard app as well. To stay completely true to the branding, we added our own versions for Light, Dark and Tinted icons instead of just relying on iOS-generated ones.
Changelog
Improvements
Customizable application icons for iOS 18 #2372
DnsLibs (DNS filtering engine)
Updated DnsLibs to v2.5.51 #2386
Scriptlets (JavaScript enhancement for filtering rules)
Scriptlets updated to v1.11.16
AdGuard pre iOS 4.5.5


Dátum vydania: 3. júla 2024
Apple fixed its iOS 17 bug that was limiting the number of Safari content-blocking rules, which contradicted their own Safari Content Blocking API documentation. That lets us remove our temporary workaround for that problem. In short, that means you can finally enable a large number of filters without them crashing, thanks to the fact that all of the 900K rules (provided by 6 AdGuard content blockers) are available again, as they are supposed to. Also, we updated Scriptlets — one of the essential libraries needed for the app’s stable performance.
If you are using iOS 17, please note that for this fix to work you need to update to the latest iOS.
If you are using iOS 16 and below, this bug doesn’t affect you.
Changelog
Fixes
Some filter rules are not applied when a large number of filters is enabled #2346
Scriptlets (JavaScript enhancement for filtering rules)
Scriptlets updated to v1.11.1
AdGuard pre iOS 4.5.4


Dátum vydania: 7. júna 2024
The app now runs more smoothly thanks to this minor update, which fixes a number of bugs.
AdGuard pre iOS 4.5.3


Dátum vydania: 12. apríla 2024
This release brings important improvements for the DNS protection feature: thanks to the DnsLibs update, there are no more DNS leaks and connection instability when changing networks. We also updated two other libraries that are essential for the app’s performance: TSUrlFilter and Scriptlets.
Starting with this version, AdGuard for iOS supports only iOS 13 or later.
Changelog
Updated Scriptlets (JavaScript enhancement for filtering rules) to v1.10.25
Updated TSUrlFilter (Advanced protection filtering engine) to v2.2.18
Updated DnsLibs (DNS filtering engine) to v2.5.17 #2314
It brings the following changes:
Improvements
Allowed specifying tcp-only and udp-only DNS upstreams #208
Fixes
Unable to use DoH DNS server that uses HTTP/1.1 since updating to version 4.3 #216
adguard_dns segfaults while acquiring mutex in
ag::dns::DohUpstream::Http3Connection::on_expiry_update() #212Unable to access Korean websites after latest version update #5120
Adblock syntax rules with FQDN don’t work #210
Other
AdGuard pre iOS 4.5.2


Dátum vydania: 11. decembra 2023
In this version, we’ve added HTTP basic authentication for DNS-over-HTTPS. This is useful if you have your own DNS server and don’t want someone else to use it. There is a nuance, though: there are not many DNS servers that support this feature right now. But soon they’ll become available in AdGuard Home and AdGuard DNS, so stay tuned!
Changelog
Fixes
Advanced rules do not work if a rule contains www. at the beginning #1897
When opening a Live video on YouTube through AdGuard, an error appears #2254
DnsLibs (DNS filtering engine)
Updated DnsLibs to v2.4.18
Scriptlets (JavaScript enhancement for filtering rules)
Updated Scriptlets to v1.9.101
AdGuard pre iOS 4.5.1


Dátum vydania: 2. novembra 2023
This update brings no major changes, but the ones it does bring are still pretty important, especially since we apparently found an iOS 17 bug as a by-product of preparing this release.
Apple, what happened to the promised 150k content-blocking rules cap in Safari?
The main attention goes to the fix of an issue on iOS 17 where filters would just update infinitely without actually updating, and, surprise, surprise, the underlying problem turned out to be on iOS’s side: using our standard Safari content blockers with 150k filtering rules all of sudden started causing a crash on iOS 17. We found out that this was happening because Safari wouldn’t accept files over a certain size anymore — even content blockers with 40-60k rules (which is 3 times below the limit) would sometimes crash, depending on the rules they contain.
As a temporary measure, we restricted the size of our JSON files and optimized main filters so that they can squeeze into this new size requirement. If a content blocker is still a little too big for Safari (the final size depends on how many and what filters are enabled by the user), we automatically cut its size so that at least part of the rules that meet the size requirement is applied.
And since it’s an obvious iOS 17 bug, we already reported it on Apple’s forum.
Read a more detailed rant about this in our blog article on v4.5.1.
Other improvements
Also, we updated SafariConverterLib, Scriptlets, and TSUrlFilter dependencies. In simple words, the update of these three components helps maintain high filtering quality, i.e. efficient and up-to-date performance of blocking rules. SafariConverterLib converts AdGuard filtering rules into Safari content blocking rules, Scriptlets and TSUrlFilter help implement the Advanced blocking feature in AdGuard for iOS.
And last but not least, two things: DnsLibs v2.3 update improves AdGuard's DNS-over-HTTP/3 performance and stability, and we also fixed the issue where AdGuard wouldn’t open on iOS 13.x.
Changelog
Improvements
Updated TSUrlFilter, Scriptlets, and SafariConverterLib dependencies #2228
Fixes
Allowed specifying the final CB JSON file size limit in order to make Safari accept AdGuard’s content blockers #56
Infinite filter updates on iOS 17 #2188
Unable to open AdGuard v4.5.0 for iOS on iOS 13.x #2194
Updated DnsLibs (DNS filtering engine) to v2.3
AdGuard pre iOS 4.5.0


Dátum vydania: 5. júla 2023
We are thrilled to announce the release of AdGuard v4.5 for iOS, which includes major changes and new features.
System-wide tracking protection
AdGuard v4.5 for iOS now includes system-wide tracking protection, which allows you to block in-app trackers that can discreetly collect user data. We are proud to introduce this great achievement to you.
In this version, we have added statistics on blocked requests to the app (see the Activity tab). We have changed the counters on the main screen to show how many trackers are blocked and how much traffic is saved.
Besides, if you now install AdGuard for iOS or reset its settings to default, the AdGuard DNS filter will already be enabled. What does this mean for you? If you turn on DNS Protection, AdGuard will automatically start blocking ads and trackers in all apps — not just Safari. It doesn't matter which server you use — the DNS traffic will be filtered anyway.
DNS-over-HTTP/3 support
In AdGuard v4.5 for iOS, we have added support for DNS-over-HTTP/3 due to the DnsLibs update. DNS-over-HTTP/3 is a newer version of the DNS-over-HTTPS protocol. AdGuard has become one of the first to support it, along with Google and Cloudflare.
Changelog
Fixes
No rules on the Content Blockers screen #2012
Versions
Updated DnsLibs to v2.2.8 #2171
AdGuard pre iOS 4.4.6


Dátum vydania: 11. apríla 2023
Spring is the time for renewal, and AdGuard products are no exception.
We've updated all the libraries used in the app and improved the UI, so now AdGuard for iOS runs smoother and is more user-friendly.
Advanced blocking rules acceleration
The Advanced Protection feature is something we're proud of and what sets us apart from other content blockers on iOS. With this module, AdGuard for iOS can apply advanced filtering rules that supplement standard Safari content blocking rules and help effectively tackle complex and encrypted ads.
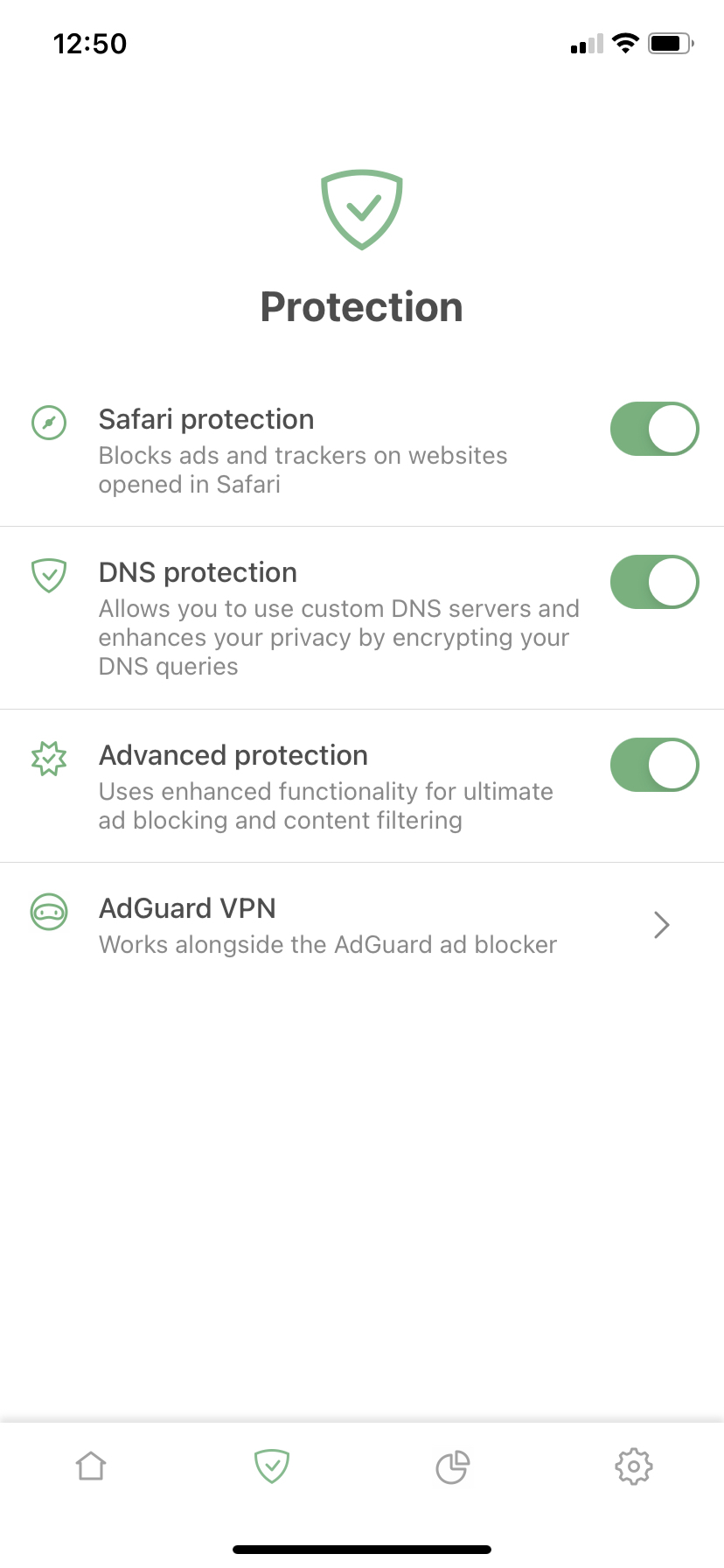
However, due to the peculiarities of iOS, the Advanced Protection feature’s operation was always limited compared to other versions of AdGuard. For example, some rules applied noticeably later than page load. Sometimes this led to ad "flickering" as it was only hidden after page loading. In other cases, this even prevented certain ads from being blocked.
When preparing the new version of AdGuard for iOS, we put in a lot of effort into speeding up the implementation of advanced blocking rules which directly improved the overall app performance. We hope you'll notice the difference.
Native support for the :has() pseudo-class
With Safari v16.4, content blockers gained the capability to select elements for hiding using the
:has() pseudo-class. While this might sound complex and confusing, it's essential to know that this feature is incredibly important to us. It allows for the selection of ad blocks based on their content. Until AdGuard v4.4.6 for iOS, support for the
:has() pseudo-class was implemented as part of the Advanced Protection module, available only in paid version. Now, this functionality is available to all AdGuard for iOS users!Changelog
Features
Show SafariConverterLib version after tapping the app version in About #2050
Show Scriptlets and ExtendedCss versions in About #2121
Improved Safari Web Extension initialization speed
Fixes
Incorrect description of Alternative servers in Spanish #2078
Versions
Updated DnsLibs to v2.0.75 #2111
Updated ExtendedCss to v2.0.51
Updated Safari Converter Lib to v2.0.39
Updated Scriptlets to v1.9.1
Updated DNS stamps for DNSCrypt
AdGuard pre iOS 4.4.5


Dátum vydania: 24. novembra 2022
In this version we've significantly updated our DNS filtering library — DnsLibs — so it consumes less resources and runs faster.
Besides, the DNS-over-QUIC protocol implementation now supports RFC 9250 (proposed standard), and the experimental status was removed from DoQ support.
Finally, we've updated our Safari rules engine and fixed a couple of bugs.
Changelog
Updated
DnsLibs to v2.0.58
AdGuard pre iOS 4.4.4


Dátum vydania: 28. septembra 2022
In this version we’ve updated the filter libraries and fixed the YouTube player on iOS 16.
Now you can watch videos ad-free right in the AdGuard app. To do this, tap “Share” in the YouTube app, tap “More”, and select “Block ads on YouTube (by AdGuard)“.
AdGuard pre iOS 4.4.3


Dátum vydania: 30. augusta 2022
This version brings the updated rule converter library and some important improvements to the Advanced protection module.
Please note that if you're updating from v4.4.0 you may need to re-enable AdGuard content blockers in Safari settings and check for filter updates in the app.
AdGuard pre iOS 4.4.1


Dátum vydania: 3. augusta 2022
This is the first update AdGuard for iOS gets since changing the developer account. Please note that you may need to re-enable AdGuard content blockers in Safari settings and check for filter updates in the app.
AdGuard pre iOS 4.4.0


Dátum vydania: 8. mája 2022
Meet AdGuard v4.4.0 for iOS! In this release we have fixed only one, but incredibly annoying issue with AdGuard DNS filtering module handling network changes. Now everything works without glitches and we can finally relax (for a while). Hope you will enjoy the new version.
Changelog
AdGuard pre iOS 4.3.3


Dátum vydania: 2. marca 2022
This update is small but important: the fixes we've made will definitely make AdGuard work even better. In this version we've improved DNS filtering to make it more stable even when the internet connection is poor. We've also fixed a bug that was preventing filter updates on iOS 15.4 beta and a couple of background crashes. And we've added some other minor improvements to make using AdGuard more comfortable.
Changelog
[Enhancement] Updated DnsLibs to v1.7.11 #1951
[Fixed] Crash due to an invalid filtering rule in the EasyList Cookie List #1941
[Fixed] Common crashes in AdGuard v4.3.2 beta #1925
[Fixed] NetworkUtils.init crashes on iOS 12.5 #1938
[Fixed] Bug with the manual refresh icon iOS 15.4 beta #1926
[Fixed] The app crashes if you add a custom filter list with empty lines #1918
[Fixed] Tunnel is being killed due to exceeding memory limit #1935
[Fixed] VPN profile won't connect after settings reset #1952
AdGuard pre iOS 4.3.2


Dátum vydania: 7. februára 2022
Not all our updates are flashy and eye-catching, but they all make AdGuard better. So, meet AdGuard v4.3.2 for iOS — right from the oven. In this release we've mainly focused on improving the app’s performance and fixing minor bugs. You'll probably notice that AdGuard now starts faster than before. We hope you’ll enjoy the new version of AdGuard for iOS.
[Fixed] No Internet when using cellular connection (DNS64 network) #1901
Previously, DNS protection didn't work with some cellular operators with IPv6-only networks (e.g., T-Mobile US). A little AdGuard magic and everything works as it should.
[Fixed] Crash on opening an app with a large DNS blocklist #1883
Now you won't have any problems if you actively use DNS protection and your custom rules.
Changelog
[Enhancement] Updated DnsLibs to v1.7.3 #1916
[Fixed] Allowlist and Blocklist disappear after reboot #1907
[Fixed] Crash in getRulesCountForFilter on empty rule lines #1918
[Fixed] Filter lists update/toggle causes noticeable battery drain #1891
[Fixed] Popular crashes in AdGuard v4.3.2 beta #1925
[Fixed] The app crashes when launched in Persian #1922
[Fixed] VPN tunnel does not restart on a network change #1892
[Fixed] iOS widget shows "Unable to Load" message, while AdGuard works correctly (fixed in most of the cases) #1849
[Other] Safari Web Extension's protection toggle button does not work on iPad OS #1878
AdGuard pre iOS 4.3.1


Dátum vydania: 29. decembra 2021
In this update we make an emphasis on fixing the bugs that we let through in the v4.3. Besides that, despite the very little amount of time that had passed since the previous update, we managed to make some changes that tangibly improve the overall quality of the app.
AdGuard pre iOS 4.3.0


Dátum vydania: 23. decembra 2021
It's time for the long-awaited release of AdGuard v4.3 for iOS. We've implemented support for AdGuard’s Safari Web Extension for iOS 15 and added Advanced protection. Never before has AdGuard for iOS blocked ads so effectively!
[Enhancement] Safari Web Extension for iOS 15
The AdGuard Web Extension for Safari serves to enhance the capabilities of the AdGuard for iOS app. With this extension, AdGuard can apply Advanced protection to better block ads in Safari, including YouTube ads, thanks to an improved filtering mechanism.
We’ve also performed a complete code refactoring and added an option to choose the filter update check interval in Low-level settings. And, of course, we fixed a few minor bugs in the process.
We hope you will enjoy AdGuard v4.3 for iOS!
Changelog
[Enhancement] "Dns filters" adding logic
[Enhancement] Descriptions are moved under headers in all sections
[Enhancement] DNS filter dialog box
[Enhancement] License screen has been reworked
[Enhancement] Design of the update icon
[Enhancement] Safari Web Extension for applying advanced rules (extended CSS, scriptlets, etc) #1794
[Enhancement] Onboarding screen text has been changed
[Enhancement] Purchase screen has been reworked
[Enhancement] iOS 15: the text in the system settings is now different #1822
[Enhancement] Handle
adguard:add_dns_server URLs[Enhancement] Video tutorial about how to block ads has been updated
[Enhancement] Leave a feedback and Report a bug options are now merged
[Enhancement] "The rule was added/removed/changed" dialog has been improved for extension
[Enhancement] AdGuard DNS filter has been added as a default one
[Enhancement] Status bar notifications are enabled by default
[Enhancement] Content blockers screen has been reworked
[Enhancement] Guide text for iOS 15 has been changed
[Fixed] The app crashes when adding a custom DNS server from an unreachable network #1730
[Fixed] DNS filter lists are updated on the disk without reloading DNS filtering which causes random filtering issues #1732
[Fixed] Fix a bug in the "Edit the DNS server" dialog
[Fixed] Migration of DoQ upstream does not work with v4.2 #1766
[Fixed] SIGPIPE crashes #94
[Fixed] Autoupdate is not working in background #1828
[Fixed] Filters update status switches from "not found" to "No filters updated" #1729
[Fixed] AdGuard can't start in portrait mode with Korean locale #1785
[Fixed] AdGuard restarting twice while playing game #1806
[Fixed] App restarting every 3 minutes #1810
[Fixed] Security filters get disabled after AdGuard reload #1811
[Other] Remove the link to AdGuard VPN app if the region of App Store is Chinese #1830
[Other] DnsLibs updated to version 1.6.71 #1853
[Other] "Reset statistic" button is hidden for free users
AdGuard pre iOS 4.2.2


Dátum vydania: 21. septembra 2021
A minor update. We changed one line to be consistent with iOS 15.
Our current focus is v4.3; it has a cool innovative feature that augments ad blocking quality. We intend to release it in the next few weeks. Stay tuned!
AdGuard pre iOS 4.2.1


Dátum vydania: 6. augusta 2021
This is a rather small update. We stopped a nasty bug in its track: DNSLibs used to return an error after an attempt to add a DNS-over-QUIC server. Now it’s fixed, so you can live in peace and use the app that has become even more bug-free. Plus, a bunch of crashes are dealt with.
[Enhancement] Update DnsLibs to 1.6.20 #1802
AdGuard pre iOS 4.2.0


Dátum vydania: 10. júna 2021
In this version we focused on improving filtering in Safari. In parallel, we solved the problem with YouTube ads that AdGuard users had been encountering. We’ve developed two ways to block them: a shortcut, the instructions for which can be found on our blog, and a Safari extension.
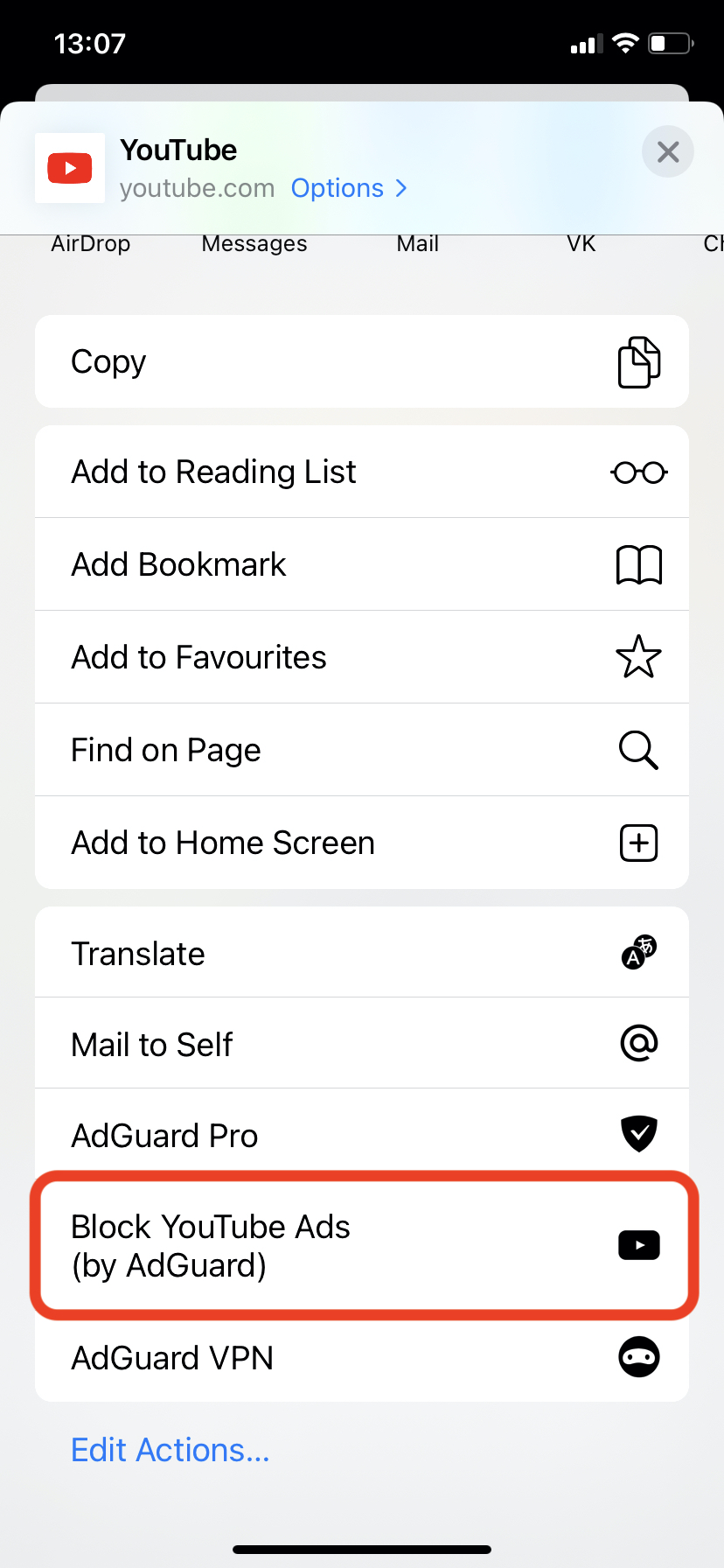
[Enhancement] Added a new action extension for blocking YouTube ads in Safari #1763
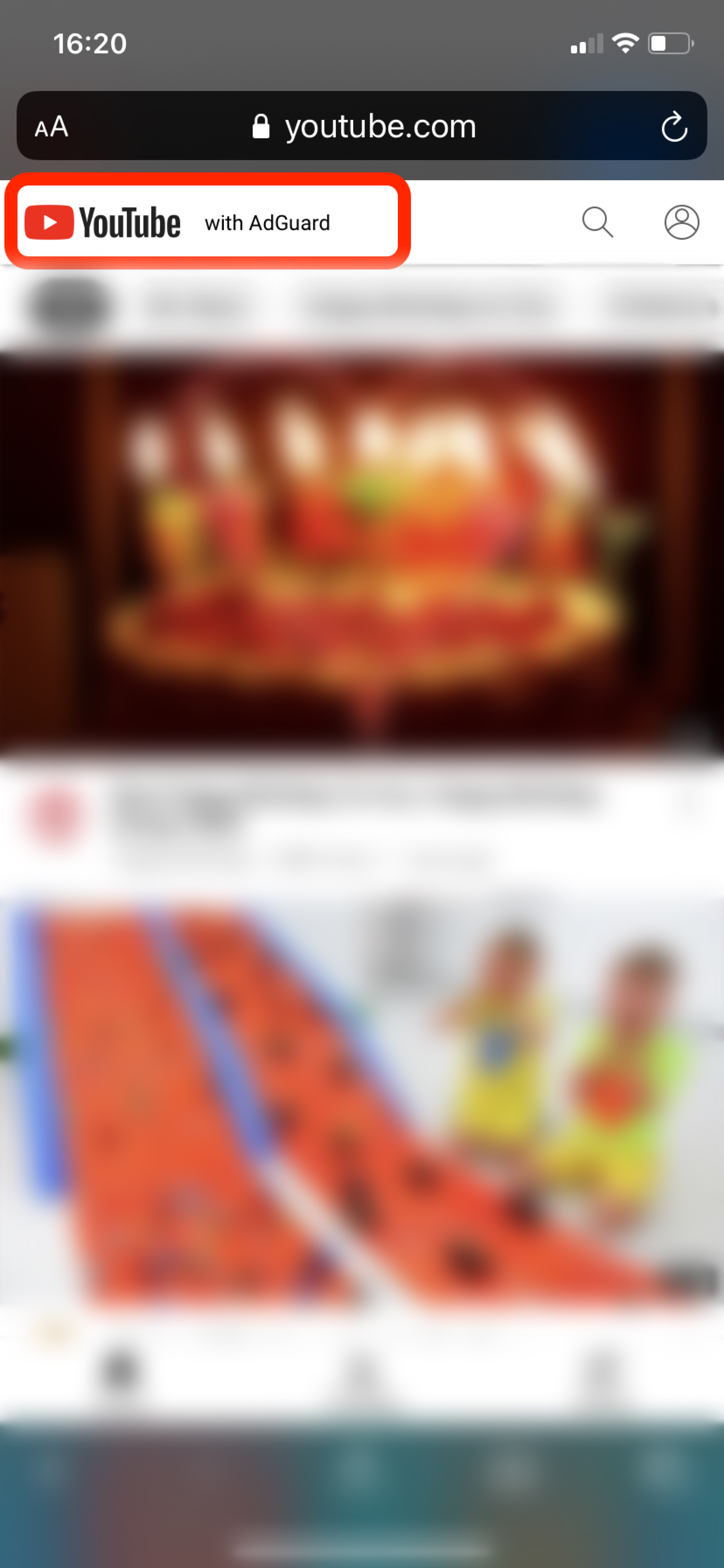
The new extension is designed specifically to block ads on YouTube in Safari and runs only there. Unlike the shortcut, the extension is built into the app, so you don’t need to install it manually. To block ads on YouTube, tap the “Share” button and select “Block ads on YouTube (by AdGuard).” After that, the “with AdGuard” caption will appear next to the YouTube logo. If it’s not there, you’ve probably reloaded the page and need to activate the extension again.
Changelog
[Enhancement] Dark/light theme switch
[Enhancement] Searching for filters in Safari protection
[Enhancement] Redesigned the Support section
[Enhancement] Marked the low-level settings that won't work in Native Implementation #1726
[Fixed] There are no notifications when activating a new device in Setapp with the maximum number of devices
[Fixed] AdGuard DNS protocols block the Internet access for third-party VPNs #1707
[Other] Added a notification for the new Safari extension
[Other] Removed “Logout“ from the About screen
Updated DnsLibs to v1.5.44 #1771
[Enhancement] Always use the local DNS resolver announced by DHCP for all queries ending with the primary DNS suffix #100
SafariConverterLib update v1.1.28
[Enhancement] Added
$denyallow modifier support #5[Enhancement] Allowed
*## cosmetic rules #11[Enhancement] Added generic CSS exclusions #15
[Fixed] Added
$specifichide modifier support #6[Fixed] Issue with long multi-domain element hiding rules #8
[Fixed] Element hiding rule with few selectors converted to an incorrect rule #21
[Fixed] The rule with
$ping blocks the whole page #14
AdGuard pre iOS 4.1.1


Dátum vydania: 22. marca 2021
This is a minor release that contains bug fixes, UI improvements, and more.
[Enhancement] Statistics is displayed as integer numbers
[Fixed] DNS filter lists are updated without reloading DNS filtering which causes random filtering issues #1732
[Fixed] The app crashed when removing a DNS blocklist #1731
[Fixed] When changing from AdGuard implementation to Native, VPN remains enabled
[Fixed] A bug when searching by tags
[Fixed] Internet connection is broken after filters update
[Fixed] Main page icons don't work correctly
[Fixed] VPN icon is not shown in Full-Tunnel mode
[Other] VPN tunnel reconnects every time the app is restarted or opened from the app switcher 4.1.1 (660) #1734
AdGuard pre iOS 4.1.0


Dátum vydania: 18. februára 2021
Long time ago scientists discovered an interesting phenomenon. While we typically think that what we most want is to actually get what we want, the most intense source of pleasure is in looking forward to getting what we want. That's the dopamine system, also known as the wanting system.
It's been months since Apple added native DNS encryption support to iOS and you might've thought that we at AdGuard just have been lazy not adding support too? Not at all! We've just been trying to follow science and provide you with as much pleasure as possible. Finally, the intensification period ends and catharsis begins!
Native support for encrypted DNS #1589
So in 2020 Apple platforms started natively supporting encrypted DNS. Namely, two protocols were supported — DNS-over-TLS and DNS-over-HTTPS (DoT and DoH). Earlier you could set up and manage DNS profiles in AdGuard. Yet, the solution wasn’t so snorky. Now we've made things simple: there is no need to download and install DNS profiles, just enable Native implementation in AdGuard for iOS settings:

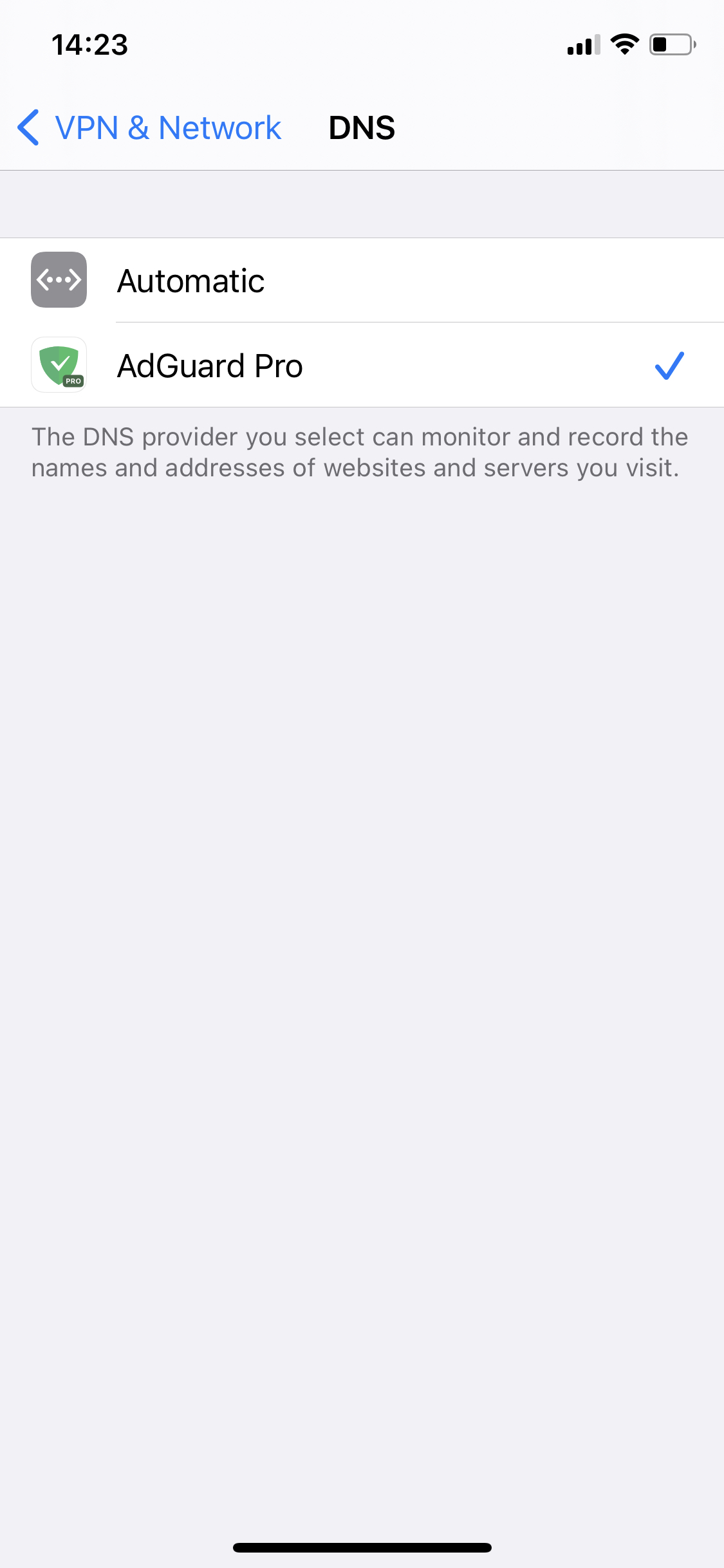
The new method of setting up DNS isn't really superior to the one you're already familiar with, but it has one slight advantage: the DNS is handled by the system and not the app. This means that AdGuard doesn't have to create a local VPN. Sadly, this will not help you circumvent system restrictions and use AdGuard alongside other VPN-based applications — if any VPN is enabled, native DNS is ignored. Consequently, you won't be able to filter traffic locally or to use our brand new DNS-over-QUIC protocol (DoQ).
Social login 📲 #1507
Now the Google login widget is present in the app (AdGuard > Settings > License > Login). A single click on a Google Sign-in button, and you're there!
For a successful login, you should have an AdGuard account registered to your Google email address. Otherwise, there will be an error.
Don't have an AdGuard account? Create one at my.adguard.com first, then you'll be able to bind it to your Google account.
Low-level stuff. ☢ For geeks only!! 🤓
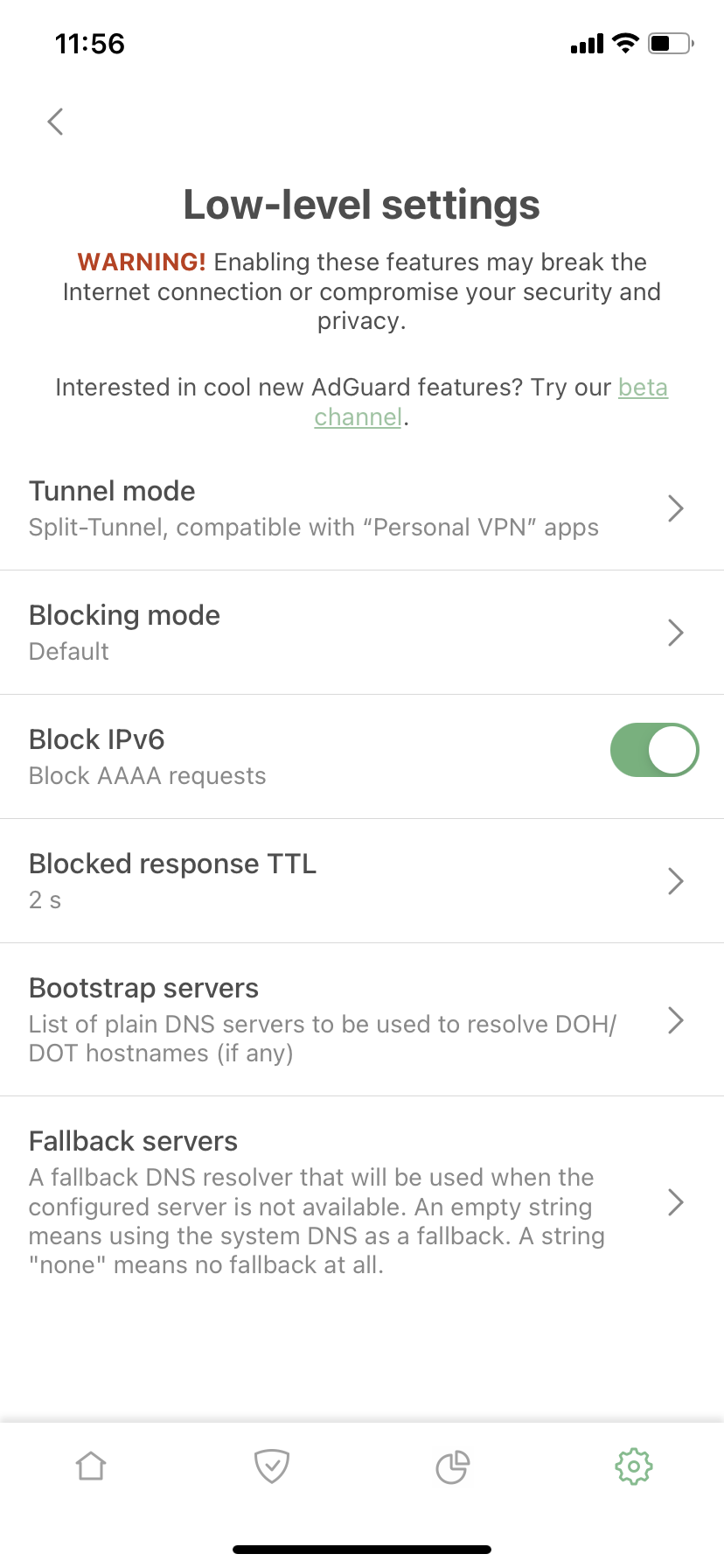

Blocking mode, Block IPv6, Blocked response TTL, Bootstrap and Fallback servers — all settings on this screen are new, except for the Tunnel mode.
Bootstrap and Fallback
Fallback is simply a backup DNS server. If you chose a DNS server and something happened to it (whatever the reason), a fallback is needed to set the backup DNS server until the main server responds.
With Bootstrap, it’s a little more complicated. For AdGuard for iOS to use a custom secure DNS server, our app needs to get its IP address first. For this purpose, the system DNS is used by default, but sometimes this is not possible for various reasons. In such cases, Bootstrap could be used to get the IP address of the selected secure DNS server. Here are two examples to illustrate when a custom Bootstrap server might help:
When a system default DNS server does not return the IP address of a secure DNS server and it is not possible to use a secure one.
When our app and third-party VPN are used simultaneously and it is not possible to use System DNS as a Bootstrap.
Block IPv6 🔒 #1289
For any DNS query sent to get an IPv6 address, our app returns an empty response (as if this IPv6 address does not exist). Now there is an option not to return IPv6 addresses.
Does anybody actually read these? ┬──┬ ノ( ゜-゜ノ)
AdGuard pre iOS 4.0.4


Dátum vydania: 15. decembra 2020
This release is mainly focused on bug fixes and minor improvements. Yet, it has a feature that one can’t ignore — DNS-over-QUIC support!
[Other] DNS-over-QUIC support (AdGuard DNS)
The first thing you should know about DNS-over-QUIC (DoQ) is that it's a new encryption protocol. Not as new as a concept, but very new in terms of practical application. In fact, AdGuard introduced the very first public DNS servers that support DoQ! The feature is still experimental — AdGuard for iOS is one of the first open-source implementations of DNS-over-QUIC — but it's perfectly functioning and we encourage you to try it.
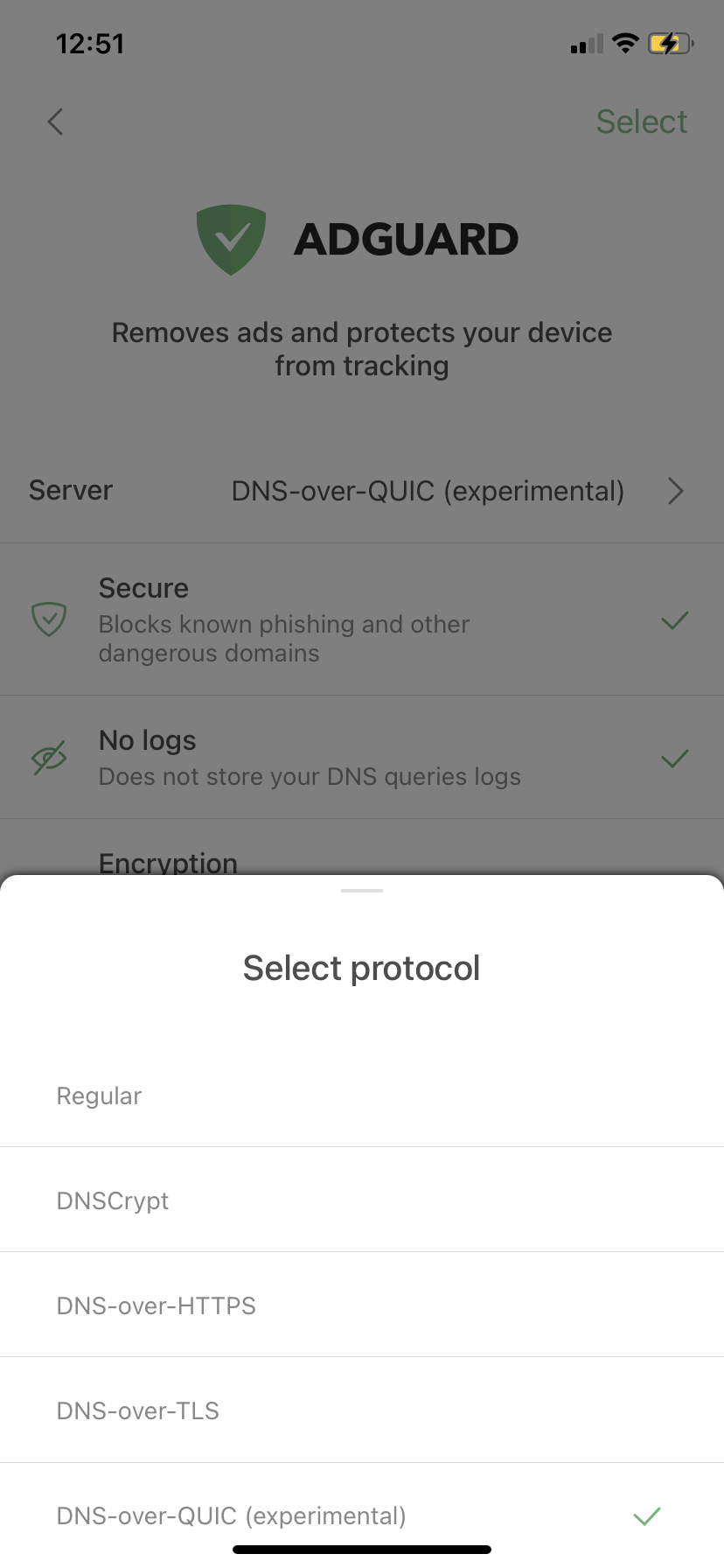
The most common DNS encryption protocols are DNS-over-HTTPS and DNS-over-TLS (DoH and DoT correspondingly). What makes DoQ special? A bunch of things: out-of-the-box encryption, reduced connection times, and better performance in cases of lost data packets.
Changelog
[Enhancement] Shown the link in the details of custom filters #1529
[Enhancement] Added "Acknowledgments" link to the "About" screen
[Enhancement] Added our discuss page URL to the "About" screen
[Enhancement] Improved the way DNS queries are logged to the Tunnel log
[Fixed] Access to the DNS Allowlist crashes AdGuard Pro #1655
[Fixed] AdGuard does not automatically select a DNS server when deleting the custom DNS server in use #1657
[Fixed] Disabling "Advanced mode" in settings disables "Auto-Update over Wi-Fi only" too #1662
[Fixed] Attempt to open "License" section causes the app crash #1664
[Fixed] Reset settings leads to broken DNS servers settings
[Other] Updated DnsLibs to 1.3.24 #1638
[Other] Incorrect record color in the Activity log
[Other] Missing image in front of "Security" filters
[Other] Circles loader updates infinitely
AdGuard pre iOS 4.0.3


Dátum vydania: 22. septembra 2020
This is mostly a bugfix release, yet it has a new handy feature — namely, custom URL scheme support. This allows you to easily add custom filters from the browser and add custom DNS servers using stamps.
Changelog
[Added] Custom URL scheme support
[Changed] Move "About" menu item to the bottom of the list
[Changed] Remove unnecessary scrolling in Settings
[Fixed] Obsolete filters were not deleted after update in some cases
[Fixed] Estonian filter icon uses flag of Ethiopia #1636
[Fixed] Localization issues #1626
[Fixed] Lost network connection when automatically switching networks (with IPv6) #1592
[Fixed] The "Remove VPN profile" button doesn't work #1625
AdGuard pre iOS 4.0.2


Dátum vydania: 18. augusta 2020
AdGuard v4.0.2 for iOS is more focused on bug fixes, yet it has some important changes. We’ve made UI improvements, redesigned the menu logic and added one more DNS server to Cloudflare. A small, but much-needed release – the first one after the long-awaited AdGuard Pro update.
Changelog
[Enhancement] Implement Cloudflare 1.1.1.1 for Families #1536
[Enhancement] Return color highlight for domains being resolved by DNS server #1579
[Enhancement] Change the way Activity screen refreshes
[Enhancement] User interface improvements and redesigned menu logic
[Fixed] DNS deactivation issue #1614
[Fixed] Lost network connection when automatically switching networks (with IPv6) #1592
[Fixed] DNS over HTTPS and TLS are broken on iOS 14 Beta #1601
[Fixed] Handle removed obsolete filters
[Fixed] OpenDNS doesn't support DoT #1753
[Fixed] Access to DNS AllowList crashes AG Pro #1613
AdGuard pre iOS 4.0.1


Dátum vydania: 15. júna 2020
This is the first update after the release of v4.0. As usual in such cases, the accent is on bugfixes, and this time there were surprisingly few bugs to fix. We also took this opportunity to update localizations.
[Enhancement] NextDNS-specific characters are now allowed in DNS server addresses #1551
[Fixed] URL blocking rules with
$document,popup do nothing in Safari #74[Fixed] AdGuard lets you select an unsupported protocol for DNS servers #1557
[Fixed] WLAN Connection gets lost when opening AdGuard #1550
[Other] App crashes when sent to background #1544
[Other] Localizations have been updated
AdGuard pre iOS 4.0.0


Dátum vydania: 12. mája 2020
After a long struggle and countless iterations we're finally ready to present AdGuard v4.0 for iOS! It's a huge update with many, many new features, design changes, bugfixes and whatnot. Let's not forget about DNS protection: a way to have full control over DNS traffic on your device. Let's check it out:
Major design changes
Traditionally, a major version increase heralds a lot of changes regarding the UI. This time is not an exception. And we really mean a lot!
General design changes: new icon styles, new menu logic, revamped main screen
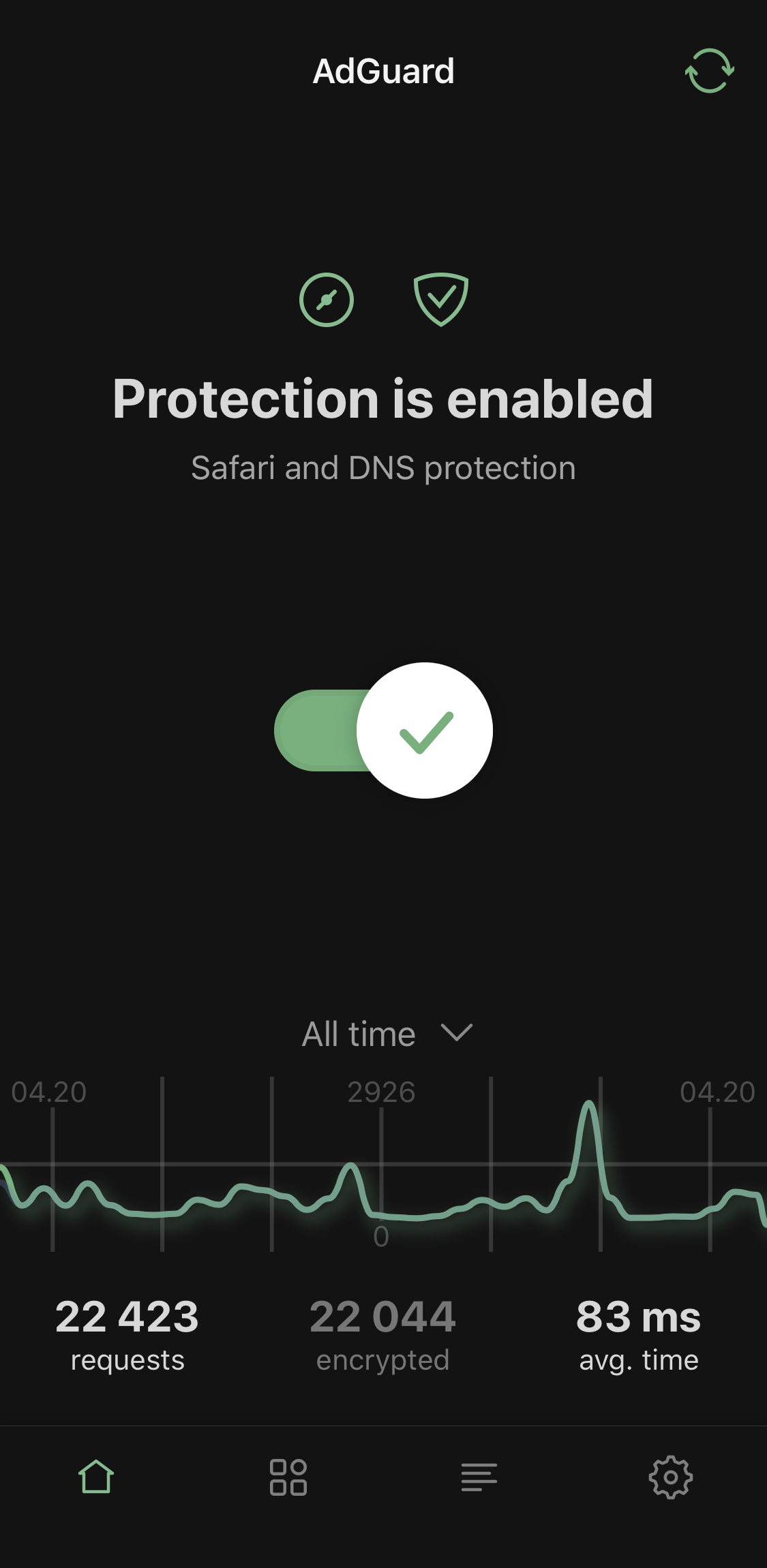
Advanced mode: additional settings for advanced users. Use at your own risk!
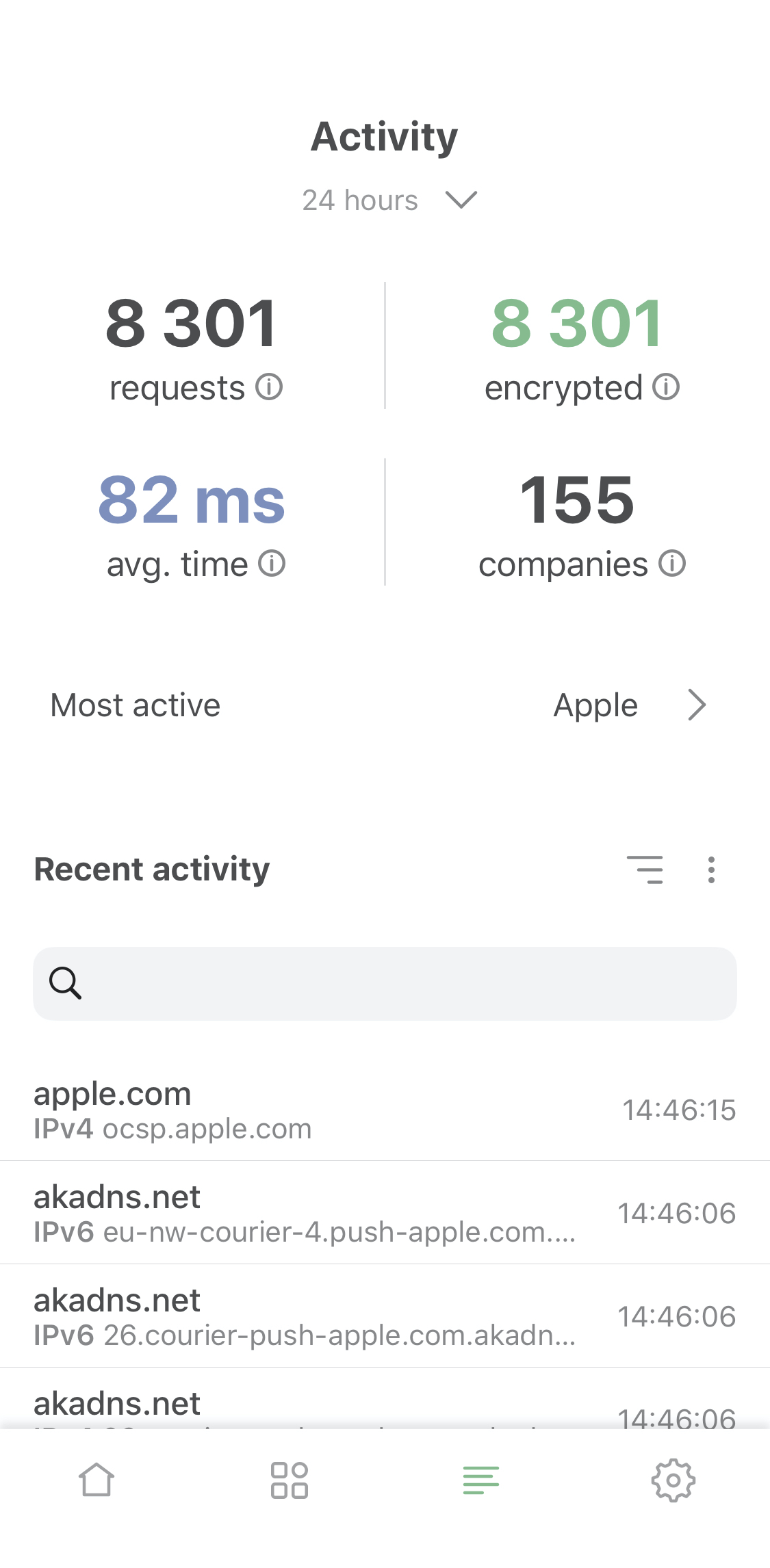
Activity feed: DNS requests log, exhaustive request details.
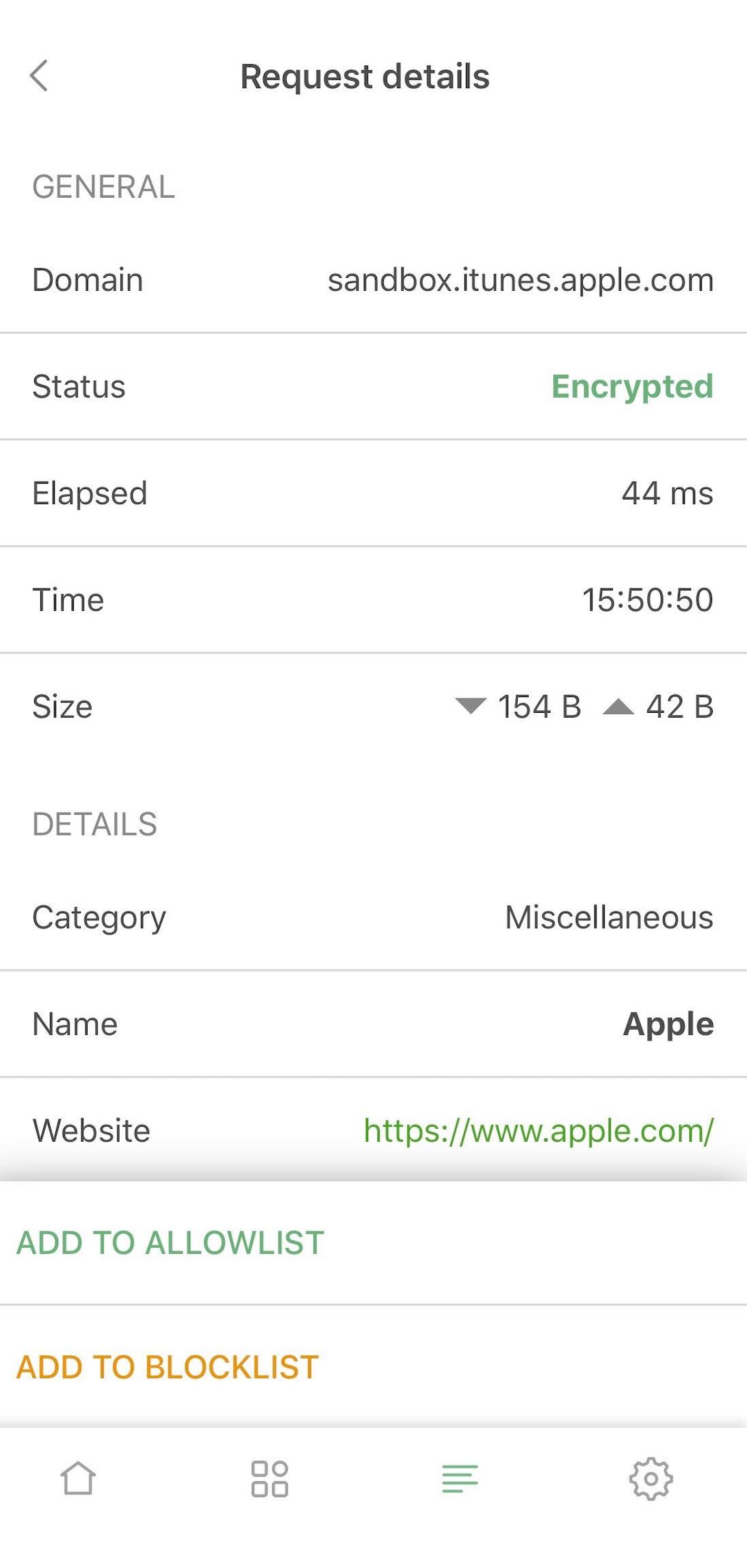
Most active companies: not only you now can see to which company this or that DNS request belongs, you can view the "leaderboard" on the 'Most active compoanies' screen, accessible from the activity feed.
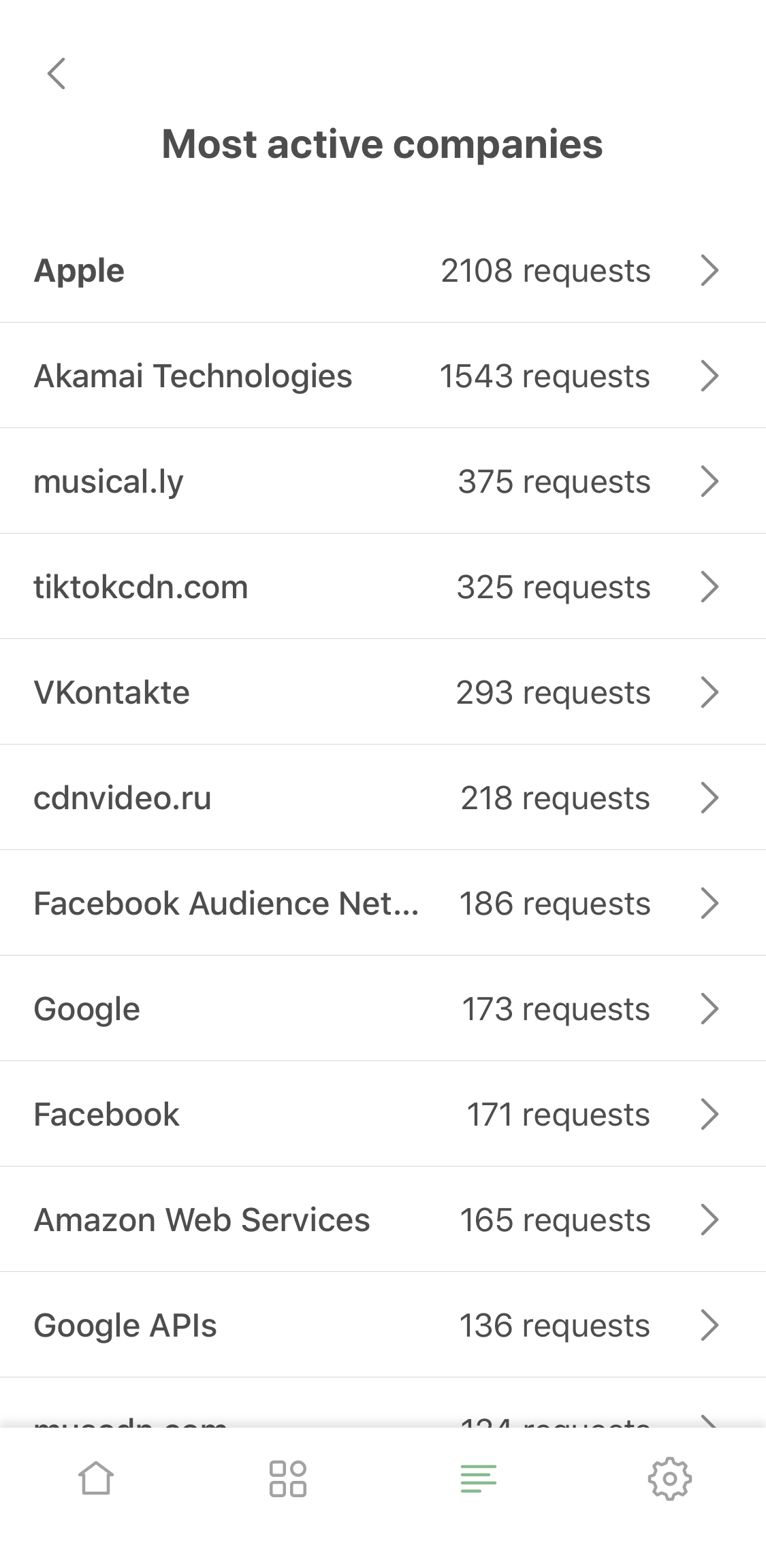
It might take a bit to get used to for the veterans, but at the same time we hope it will come very natural to new users.
Enhanced DNS protection #1107
In addition to familiar DNS functionality you now can add mobile network or certain Wi-Fi networks to exclusions. For example, you can use it if you have AdGuard Home set up for your home Wi-Fi.
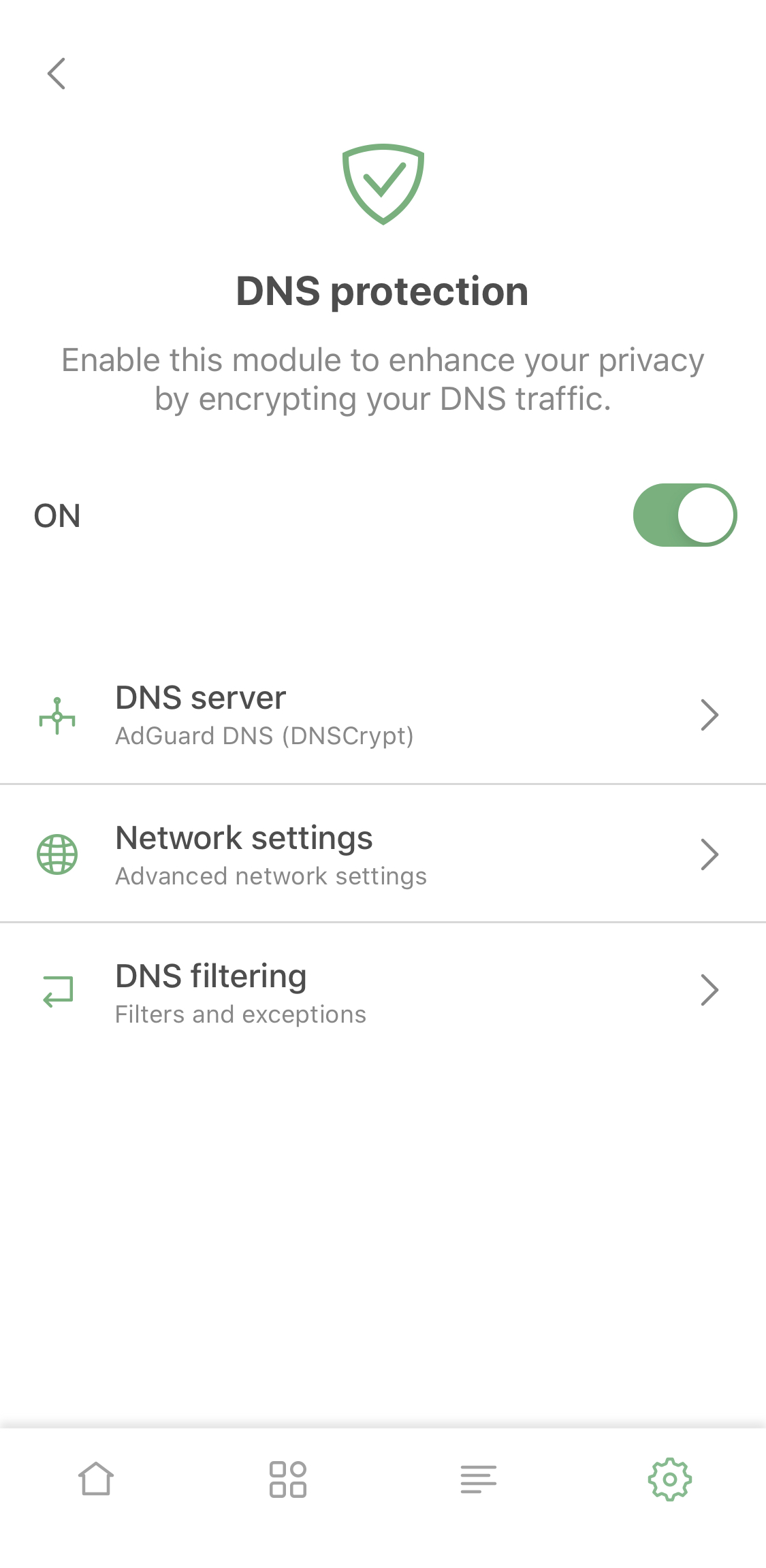
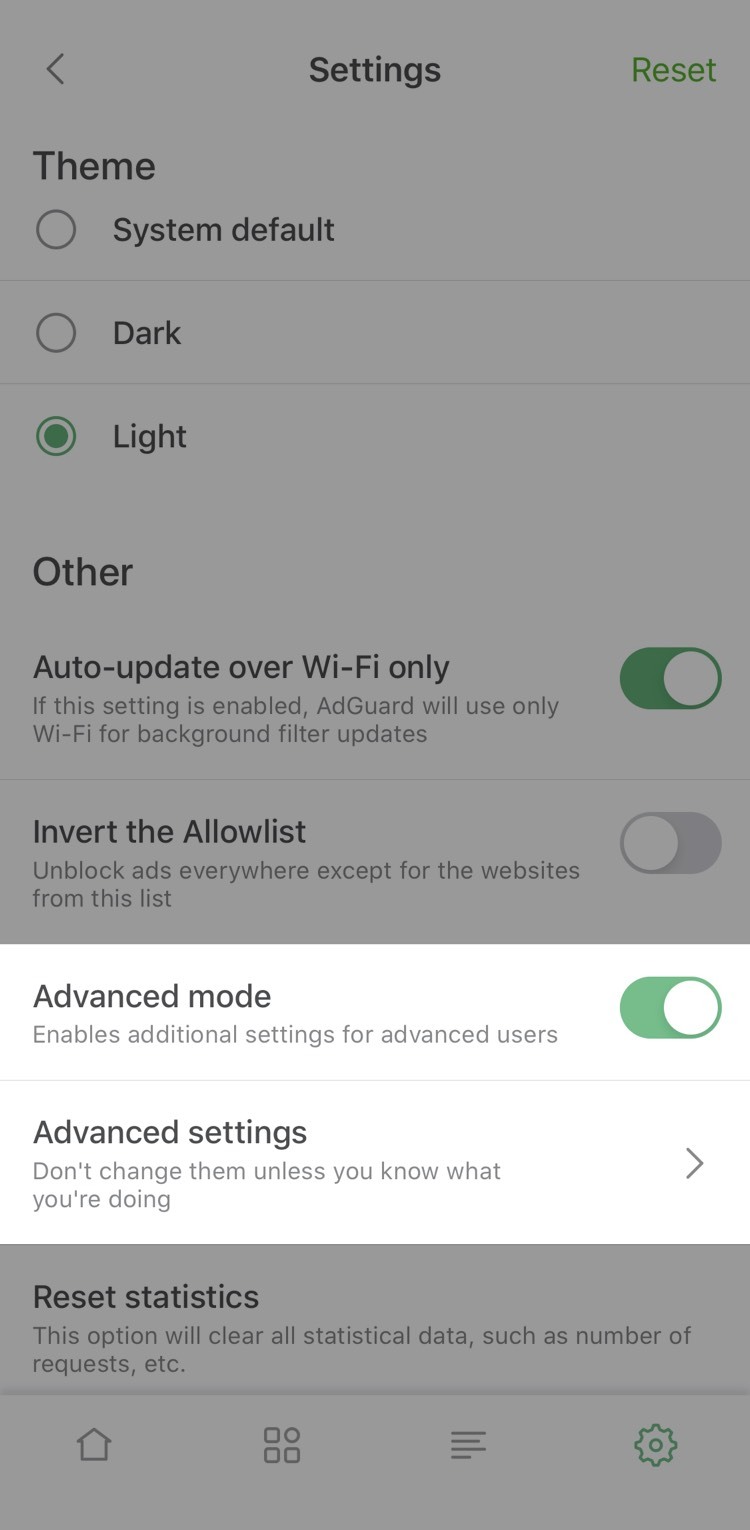
Also, by enabling 'Advanced mode' you get access to DNS filtering: add custom hosts files or filters like AdGuard SDN filter to have more agency over your DNS traffic.
New AdGuard widget #973
Now AdGuard for iOS gets its own widget, just like AdGuard Pro. Look at this beauty:
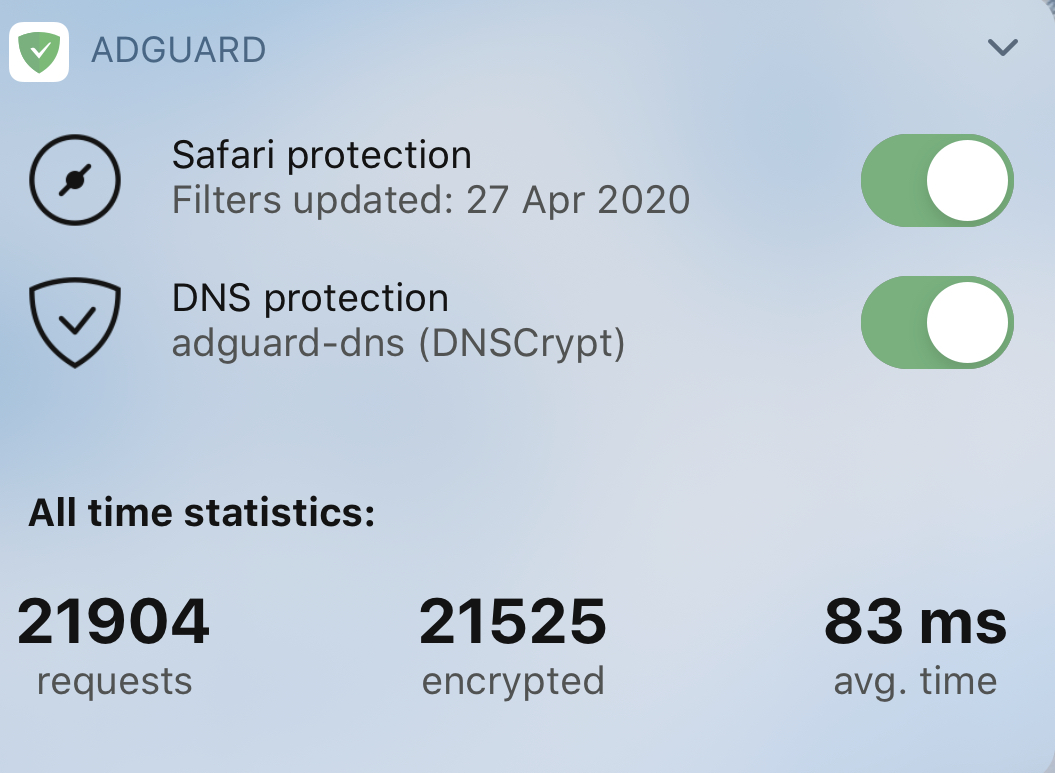
It does everything you want: provides quick access to DNS protection and Safari content blocking switches, displays current DNS server and statistics. You barely need to open the app itself!
General statistics #1325
Another previously AdGuard Pro-exclusive feature that all AdGuard for iOS users will now be able to enjoy. A curious toy for some, an instrument to control your traffic for others — everyone will find it amusing, if not useful. You’ll find the stats on the main screen of the app:
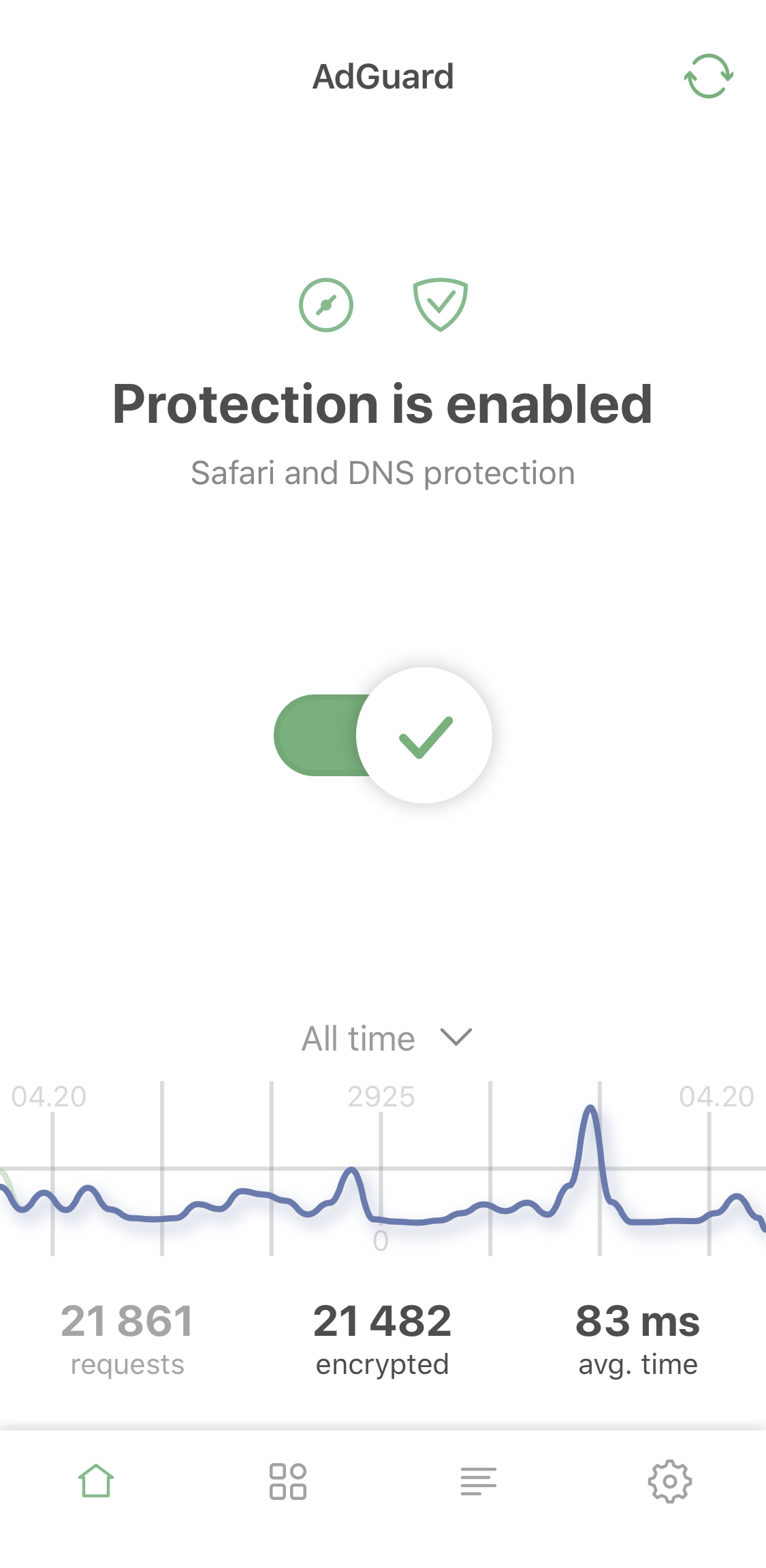
Switch between all-time, monthly, weekly or daily stats and between all or blocked requests.
Changelog
[Bug] Content Blockers screen shows User Filter as loaded even when it’s off #1287
[Bug] When reporting a website via the Action extension, the URL of the reported website is not automatically inserted #1288
[Bug] Unable to change DNS type from DoH to anything else #1347
[Bug] The app crashes after adding two rules in a row via Action extension #1426
[Bug] AdGuard doesn’t respect "Autoupdate over Wi-Fi only" setting #1381
[Bug] Wrong language icon for Liste AR filter #1334
[Bug] Filter update status is not showed properly #1364
[Bug] Endless content blocker update animation #1365
[Bug] Can't add link to the whitelist #1
[Bug] Incorrect main switch state #1517
[Bug] "Tracking Protection" doesn't automatically turn off when another app turns on a VPN #1516
[Bug] Wi-Fi exception issue #1519
[Bug] Total requests count is decreasing #1495
[Bug] Menu name disappears after adding a new DNS custom filter #1472
[Bug] 'Matched filters' in the filtering log are not shown correctly #1441
[Bug] VPN suddenly turns off in background #1508
[Bug] VPN is still enabled for some trusted Wi-Fi exceptions #1475
[Bug] Wrong switches behavior on the main screen #1445
[Bug] Entries in the inverted whitelist get deleted after an app update
[Bug] The NEXT button on the login page doesn’t switch focus to the password text field #1378
[Bug] Screen title is missing #1454
[Bug] Widget doesn’t work #1506
[Enhancement] New option to edit custom filter list names #1068
[Enhancement] New option to remove the AdGuard VPN profile #1408
[Enhancement] Pull the screen down to update DNS filters #1513
[Enhancement] UI got adapted for Screen reader #1150
[Enhancement] Filter lists now update on the app update #1481
[Enhancement] Activity for loading a new custom filter #1438
[Enhancement] DNS response status is now resolved in the tunnel extension #1355
[Enhancement] App theme now matches the system default theme after the first installation #1435
[Enhancement] Added DNS upstream validation #1436
[Enhancement] New DNS proxy library #1332
[Feature] New option to enable/disable individual rules in Safari user filter and Safari whitelist #1353
[Feature] New option to exclude Wi-Fi networks from DNS filtering #1276
[Feature] An option to reset AdGuard settings to default #1089
[Feature] Progress bar for currently running tasks #1282
[Feature] An option to reset statistics #1358
[Feature] New Activity Screen #1403
[Feature] Trackers' details #1279
[Other] New button to close Action extension #1110
[Other] An intermediate dialog for adding new rules from the Filtering log - #1389
[Other] Two separate loading screens for light and dark themes #1284
[Other] An error message is now shown after an attempt to add an invalid rule to User filter #1109
[Other] Warning too large hosts files #1474
[Other] Minor UI improvements #1501
[Other] 'Rate our app' dialog got improved #1467
[Other] Video tutorial got updated #1429
[Other] Removed 'Next' button when loading new custom filter #1438
AdGuard pre iOS 3.1.3


Dátum vydania: 5. decembra 2019
A small update aimed mostly at improving app’s stability.
[Changed] “Purchase” screen #1345
[Fixed] Several crashes #1344
[Fixed] Disabling filtering on a page via Safari action extension sometimes doesn’t work properly #1350
[Improved] Developer logs now include information about content blockers’ behavior #1346
[Improved] “Content blocker cannot be registered” case handling #1240
AdGuard pre iOS 3.1.2


Dátum vydania: 21. októbra 2019
AdGuard v3.1.2 for iOS tidies up some of the leftover bugs from the previous release.
AdGuard pre iOS 3.1.1


Dátum vydania: 1. októbra 2019
We’re fixing some bugs here that emerged after the recent v3.1 update.
[Fixed] VPN icon isn’t hidden in iOS 13 #1246
[Fixed] Rare visual glitches on iPad Pro 11" #1248
[Fixed] Mascot style doesn’t match the chosen app theme #1252
[Fixed] License expiration notification is mistakenly displayed #1267
[Fixed] Crash on the purchase screen with certain system languages #1268
[Fixed] Crash due to slow content blocking compilation #1269
AdGuard pre iOS 3.1.0


Dátum vydania: 19. septembra 2019
Apple tries to steal our thunder with their iOS 13 release, but we stay calm, as we’re sure: AdGuard 3.1 for iOS is big news! There are many noteworthy improvements to filtering process, design and licensing system. Let’s tackle the new version one change at a time.
[Added] New content blocker — Security #1103
In v3.0 we “split up” AdGuard for iOS into five content blockers to circumvent the Safari limitation on 50k rules per ad blocker (which is a ridiculously small number). Each of the content blockers was assigned a specific role, for example, “Privacy” or “Annoyances”. But then we thought: the more content blockers, the more rules you can use at the same time, right? So why not add another one? And we didn’t have to go out of our way for that, as “Security” is a category that organically complements the rest. Previously, filters from that category were included into “Other” group.
Note that you need to enable this new content blocker in Safari settings for it to work!
[Added] “Content blockers” screen #1105
It’s surely irritating when you have to go to Safari settings to check what filter groups are enabled and what are not. We know this from personal experience. The logical solution was to add a new screen right to AdGuard settings, which we did. Go to General settings > Content blockers to see the current state. You’ll even find there what filters exactly are enabled and how many rules each content blockers has used up.
[Improved] Protection status notification on the main screen #1106
This is another change that was so easy to make that it left us wonder why we didn’t make it earlier. Before v3.1, if any one content blocker was disabled, the main screen screamed at you with a red “Protection is disabled” warning, which is of course not true. Now it will let you know in a less alarming yellow color that “some content blockers are disabled”. We care about your mental health :D
[Improved] Content blocker affinity #1104
And here’s a very important change that affects the quality of the actual ad blocking. Some filtering rules depend on each other or work better together. There’s been a problem in cases when such rules belonged to different content blockers. They weren’t always working as intended, even if both content blockers were enabled. Now that it’s fixed, the quality of ad blocking will go further up.
[Added] Lifetime subscription option #1100
As you know, AdGuard for iOS offers two ways to activate Premium features: with a license key and via App Store subscriptions. It wasn’t very fair that while license keys can be either 1-year or lifetime, there was only a 1-year subscription-based activation option. Now, if you’re enjoying AdGuard and would like to stay with us for a while, you can purchase a lifetime subscription in App Store and save some money!
[Added] Native login screen #1197
And a small treat for our users who prefer license keys to subscriptions approach. To link AdGuard for iOS to your AdGuard personal account you don’t need to jump between the app and the browser anymore. When you tap the “Log in” button, a new screen will pop up that allows you to enter the credentials right there. You can choose the “Forgot password” option or even register a new account there too, if needed.
Ad Blocking
[Changed] The algorithm of adding a whitelist rule via the Safari action extension #1218
[Fixed] Some URL blocking rules aren’t working #1139
UI
[Added] “Filter details” screen #1122
[Added] Global search to the filters settings screen #1126
[Added] Description to the “Restart when network changes” option #1040
[Added] “Export logs” option to the “Send feedback” menu #1102
[Changed] AdGuard now asks for permission to push notifications #1053
[Fixed] Notification after successful login with license key is missing #1180
Networking
[Changed] AdGuard now makes several attempts to register a content blocker if the first one failed #1205
[Fixed] Unexpexted logout at background fetch #1183
[Fixed] Can’t add a custom rule when too many filter lists are enabled #1159
Other
[Fixed] Crash after opening “Custom filters” #1185
[Fixed] Crash when adding multiple custom filters #1035
[Fixed] Crash when tapping on “Add rule” in User filter #1137
[Fixed] DNS privacy status is displayed incorrectly #1178
[Fixed] User filter doesn't work correctly #1189
[Improved] License status is now checked on the first app startup #1198
[Improved] User filter / Whitelist rules validation process #1174
AdGuard pre iOS 3.0.1


Dátum vydania: 18. júla 2019
This update fixes a lot of small-ish bugs, this is a hotfix of sorts if you will. We started addressing iOS 13-related issues, as its gaining more and more popularity among users despite still being in beta.
[Added] Two-Factor Authentication (if enabled in Account) #985
In v3.0 we added an option to log into your adguard.com personal Account via the app to activate Premium features of AdGuard for iOS. We completely forgot to take into account that some users have had two-factor authentication configured. Now we fix this unfortunate mistake, from now on you’ll be prompted to confirm your identity with an authenticator app in such case.
Ad blocking
[Fixed] Issues with User filter #1081
UI
[Changed] Dark mode is now available without Premium #884
[Changed] A confirmation dialog is now shown when a rule was added via Safari app extension #1034
[Fixed] Wrong notification is shown on the first launch #1051
[Fixed] Assistant window #1057
[Fixed] The login form is not hidden after you log in #1078
Other
[Added] License key validation #1065
[Added] A link to the Privacy Policy in the VPN dialog #1082
[Changed] Date format for time&date of filter updates changed to Chinese in Chinese interface #913
[Changed] “Malware domains" filter list has been removed from available filters #1112
[Fixed] Domains can’t be added to Whitelist #1062
[Fixed] Tutorials crash the app on iPad OS beta #1090
[Fixed] User filter crashes when an invalid rule is added #1094
[Fixed] Manual element blocking tool doesn’t work on iOS 13 #1096
[Fixed] Sometimes authorization freezes the app #1108
[Improved] Sharing the AdGuard app link leads to bad formatting #1075
[Improved] Google DoH and DoT URLs have been updated in the configuration #1092
[Improved] Localizations has been updated
AdGuard pre iOS 3.0.0


Dátum vydania: 17. júna 2019
This is huge! AdGuard 3.0 for iOS has lots of new things that should get you excited! DNS Privacy module, custom filters and max limit count raised to 250k ー we have enough topics to talk about!
[Improved] Safari content blocker max rule count raised to 250k #819
Safari is notoriously known for its harsh 50k max limit for filtering rules in content blockers. This number is laughably low, and for ages we were struggling with it. Now we've implemented a workaround: split AdGuard into five content blockers. Each of them has the same 50k restriction but in total they add up to a reasonable 250k rules max. You don't have to seek weird compromises anymore and can enable all your favorite filters!
[Added] "DNS Privacy" settings section #887
This section should look familiar to seasoned AdGuard Pro users. Basically, this is where you have a chance to configure DNS settings the way you like it ー and further protect your privacy along the way. The main difference to the Pro version is that there's no blacklist or whitelist here, this was impossible under the current Apple policy. However, there is a requests log that will provide you information about everything that's going on on your device.
[Added] An option to import custom filters by URL #518
This option will be very useful for those who support their own filters, or just have a favorite filter that wasn't included by default. Add it by URL and it will be kept updated just as any other filter!
Ad blocking
Network
[Added] "Restart tunnel on network change" setting #1039
[Fixed] DNS Privacy switch is on after VPN configuration is deleted from iOS settings #946
[Fixed] Filters update error #930
[Improved] Support for DNS64 / NAT64 networks has been added #796
UI
[Added] An option to pause video guides #863
[Changed] Tutorial videos has been slowed down a bit #826
Other
[Added] A forwarder for AdGuard website links #783
AdGuard pre iOS 2.1.1


Dátum vydania: 22. júna 2018
We are lucky to have a lot of amazing volunteers who help us translate AdGuard into various languages. Thanks to their efforts we were able to improve the existing localizations and even add a new one — AdGuard is now available in Japanese!
[Improved] Translations have been updated
AdGuard pre iOS 2.0.5


Dátum vydania: 23. apríla 2018
Hello! This is a very small update. We updated the translations (thanks to all the volunteers by the way!) and added a "Rate me" dialog window. If you've always wanted to give us 5 stars, but just keep forgetting — this change is for you! :) Seriously though, just swipe the dialog away if you don't feel like rating the app, and it won't bother you again.
[Added] "Rate me" dialog #751
[Improved] Translations has been updated
AdGuard pre iOS 2.0.4


Dátum vydania: 29. marca 2018
Hello! Some iOS 9 users may have encountered certain troubles after the previous update. We fixed the related issues in this hotfix, so please update! Users of newer iOS versions can update too, there's no harm in that :)
AdGuard pre iOS 2.0.2


Dátum vydania: 19. marca 2018
Usually we update both AdGuard and AdGuard Pro for iOS simultaneously, but not this time. Don't worry — the new version of AdGuard for iOS has arrived, and it features new design, web reporting tool integration and more.
[Changed] App redesign #455
This is undoubtedly the first thing you will notice when you run the app after the update. Light theme has been discontinued in favor of a dark one, and the overall style of the menu has changed.
[Added] Detect if Content Blocker is not enabled in Safari settings #437
Enabling AdGuard Content blocker in Safari settings is required to have filtering going on in Safari. If AdGuard is disabled, the red warning will appear at the top of the main screen to remind you to enable the Content Blocker. The video right below it shows how to do so.
[Added] Integration with the web reporting tool #533
You may have heard about the online reporting tool before, especially if you are an AdGuard for Windows or AdGuard extension user. Basically, it is a web form to report missed ads, false positives or any other issues caused by AdGuard filters. Now it is integrated with AdGuard for iOS, so whenever you report a problem, the app will automatically prefill all the required fields about its settings.
UI
[Added] "Learn about other AdGuard products" item to the "RATE AND SHARE" block #641
[Improved] Tutorial videos have been updated #539
[Improved] AdGuard now uses default iOS Sharing functionality #590
Ad Blocking
[Changed] “Send Bug Report” menu item has been reworked #649
[Fixed] Error while loading filters into Safari #550
Other
[Improved] Translations has been updated
AdGuard pre iOS 1.3.3


Dátum vydania: 12. decembra 2017
The time has come for another version of AdGuard for iOS to be released. Renovated Assistant and the new “Invert whitelist” option are the headliners of this update.
[Changed] Assistant in the Safari extension #469
We have unified the Assistant code, so that it’s the same across the board now: AdGuard for Windows, Mac and iOS, browser extensions, you name it. While at it, we have changed the exterior a bit (hopefully, for the better). As a side effect, there’s temporarily no ‘Preview’ option, but it will be added in the next version.
[Added] Inverted whitelist #431
This is a quite narrow option, but some users will definitely find it useful. By inverting the whitelist (which you can do in the Advanced settings, by the way) you will switch AdGuard into a special mode that doesn’t block ads anywhere by default, but filters all websites that you add to this list. The inverted whitelist is independent from the regular whitelist, so you can have them both configured as you find appropriate and switch between the modes depending on your current goals.
[Improved] Added scaling support for iPhone X (18:9) #513
Upon the release of iPhone X some of AdGuard interface panels looked pretty ugly. We had to do some work to make it look smooth and natural for all those lucky owners of the newest Apple flagship device :)
UI
[Fixed] Keyboard covers up text field in custom filters #505
[Changed] Localizations have been updated
AdGuard pre iOS 1.3.1


Dátum vydania: 28. augusta 2017
AdGuard pre iOS 1.3.0


Dátum vydania: 22. augusta 2017
This is a rather small update. A couple of important fixes like broken filter search, several minor UI changes + updated translations.
[Added] A build number to About screen #406
[Added] "Filter rules syntax" link to the User filter #375
[Fixed] Filter search doesn't work #388
[Fixed] Not able to report a missed ad in Safari #394
[Fixed] Sometimes AdGuard сrashes when you open advanced settings #451
[Fixed] Incorrect warning message on the main screen about the filters conversion error #414
[Improved] The translations have been updated #427