AdGuard Home 0.107.72


출시일: 2026년 2월 25일
연중 첫 릴리스는 언제나 중요합니다. 앞으로 몇 달간의 방향성을 보여주는 출발점이 되기 때문입니다.
이 버전에서는 TLS 인증서 업데이트 처리 방식을 변경하고 몇 가지 새로운 부가 기능을 추가했습니다. 또한 구성 설정을 변경하고 보안을 강화했습니다.
앞으로 더 많은 기능이 추가될 예정이니 계속 지켜봐 주세요.
AdGuard Home 0.107.69


출시일: 2025년 10월 30일
AdGuard Home v0.107.69에서는 두 가지 성가신 버그가 수정되었습니다. 이번에는 새로운 기능은 없지만, 이제 모든 것이 조금 더 원활하게 실행될 것입니다.
AdGuard Home 0.107.68


출시일: 2025년 10월 23일
보안 업데이트를 수행했으며, DNS 재작성(rewrite) 규칙을 활성화 및 비활성화할 수 있는 새로운 옵션을 추가했습니다.
이는 기능 요청 사항 중 하나였으며, 마침내 제공하게 되어 기쁩니다. DNS 재작성(rewrite) 규칙을 일괄적으로 활성화/비활성화하거나 개별 재작성(rewrite) 규칙별로 설정할 수 있습니다. 두 방법 모두 YAML 파일 편집 또는 UI를 통해 가능합니다.
AdGuard Home 0.107.66


출시일: 2025년 9월 15일
아무리 뛰어난 소프트웨어라도 사용자가 접근할 수 없다면 소용이 없습니다. 이번 버전에서는 인증 오류 몇 가지를 우선적으로 수정하여 언제든 로그인하고 AdGuard Home을 제대로 활용할 수 있도록 했습니다. 보안 업데이트와 기타 일부 변경 사항도 포함되어 0.107.66 버전이 출시되었습니다.
AdGuard Home 0.107.64


출시일: 2025년 7월 29일
AdGuard Home의 새 버전에서 보안 버그, 캐시 응답 TTL 버그, 심지어 DNSCrypt 인증서 관련 문제 등이 수정되었습니다.
AdGuard Home 0.107.63


출시일: 2025년 6월 30일
이 버전에서는 몇 가지 버그가 수정되었으며 안정성이 향상되었습니다.
AdGuard Home 0.107.62


출시일: 2025년 5월 29일
많은 기업들이 고객 중심이라고 말합니다. 그러나 AdGuard Home은 단순한 고객 중심(client-oriented)이 아닌,
$client 중심이라고 말씀드릴 수 있습니다. 이번 버전에서는 client 수정자가 포함된 규칙이 작동하지 않는 버그가 수정되었습니다.또한 평소와 같이 Go 버전을 업데이트하여 일부 취약점을 보완함으로써 AdGuard Home의 보안을 개선했습니다.
AdGuard Home 0.107.60


출시일: 2025년 4월 17일
이 버전에서는 새로운 기능이 추가되지 않았지만, Go 취약점 패치, UI 및 Docker 업데이트, 그리고 몇 가지 버그 수정 사항이 포함되었습니다.
AdGuard Home 0.107.59


출시일: 2025년 3월 21일
이 핫픽스는 이전 버전에서 발생한 버그를 해결합니다. 이 버그로 인해 사용자는 로그 검색 창에 아무 것도 입력할 수 없었습니다. 또한 클라이언트 수정자의 잘못된 기능도 수정했습니다.
감사의 말
커뮤니티 관리자 팀인 @AdguardTeam/community-moderators와 이슈를 제기하고, 번역을 추가하고, 이 버전을 테스트하는 데 도움을 주신 모든 분들께 특별한 감사의 말씀을 드립니다!
AdGuard Home 0.107.58


출시일: 2025년 3월 20일
이번 버전에서는 많은 버그가 수정되었고, 한 가지 작은 기능이 추가되었습니다. 이 기능에 대해 자세히 설명해 드리고자 합니다.
DNS 쿼리를 확인하는 개선된 도구
개인정보 보호와 광고 차단에 대해 진지하게 생각하고 있다면 많은 필터와 사용자 정의 규칙을 가지고 있을 것입니다. 이제 필터를 설정할 때마다 특정 DNS 쿼리가 차단되는지 쉽게 확인할 수 있습니다. 기존 도구를 개선하여 DNS 레코드 유형과 특정 클라이언트(IP 주소 또는 ClientID 기준)를 지정할 수 있는 옵션을 추가했습니다. 정보를 입력하면 쿼리와 일치하는 모든 규칙을 확인할 수 있습니다. 원하는 도메인을 바로 차단 해제할 수 있습니다.
AdGuard Home 0.107.57


출시일: 2025년 2월 21일
새로운 버전에서는 웹 UI에서 업스트림 타임아웃을 지정할 수 있는 기능이 추가되었으며, 일부 버그 수정 및 보안 업데이트도 이루어졌습니다.
AdGuard Home 0.107.56


출시일: 2025년 1월 24일
새 버전에서는 새로운 API와 일부 취약점을 보완하기 위해 업데이트된 Go 버전을 사용할 수 있습니다. 또한 몇 가지 버그가 수정되었습니다.
AdGuard Home 0.107.55


출시일: 2024년 12월 12일
이번 버전에서는 일부 Windows 설치에 영향을 미치던 버그가 수정되었습니다. 또한 몇 가지 취약점과 몇 가지 유출 문제를 해결하기 위해 Go 버전을 업데이트했습니다.
AdGuard Home 0.107.54


출시일: 2024년 11월 6일
이번 AdGuard Home 버전에서는 Windows에 필요한 보안 개선이 이루어졌습니다. 또한 필터의 성능을 개선하기 위해 필터를 업데이트했으며 일부 버그도 수정했습니다.
AdGuard Home 0.107.53


출시일: 2024년 10월 3일
커뮤니티 회원들의 도움으로 두 가지 취약점을 발견하고 이를 해결하기 위해 노력해 왔습니다. 해결책을 찾는 데 예상보다 시간이 조금 더 걸렸지만 결국 새 버전을 출시하게 되었습니다.
취약점과 버그만 수정한 것이 아니라 일부 기능도 개선했습니다. 예를 들어, 안전 검색에 Ecosia 검색 엔진을 추가하고 64비트 RISC-V 아키텍처를 지원하게 되었습니다. 아래에서 전체 변경 로그를 확인하세요.
AdGuard Home 0.107.52


출시일: 2024년 7월 4일
이번 버전에서는 개발 품질과 사용자 경험을 개선하기 위해 여러 버그를 수정했고, 프런트엔드를 TypeScript로 이전했으며, 프런트엔드 라이브러리를 업데이트했습니다.
AdGuard Home 0.107.51


출시일: 2024년 6월 6일
일부 버그를 수정하고 보안을 강화하기 위해 이 버전을 출시하게 되었습니다. 향후 버전에서 새로운 기능을 추가하기 위해 노력하고 있습니다.
AdGuard Home 0.107.50


출시일: 2024년 5월 24일
지난번 AdGuard Home 업데이트 이후 일부 사용자가 AdGuard Home을 전혀 시작할 수 없었기 때문에 이번 핫픽스를 배포하게 되었습니다.
AdGuard Home 0.107.49


출시일: 2024년 5월 21일
이번 패치에서는 몇 가지 버그를 수정하고 AdGuard Home을 더 원활하게 실행할 수 있도록 했습니다.
AdGuard Home 0.107.48


출시일: 2024년 4월 5일
After the last update it became possible for banned users to make DNS queries over encrypted protocols. This behavior, of course, was not intended, and is fixed by this hotfix.
We apologize for this oversight and will do our best to avoid repeating such mistakes in the future.
AdGuard Home 0.107.47


출시일: 2024년 4월 4일
이번에는 보안 시스템을 업데이트했을 뿐만 아니라 시간대 선택 문제와 기타 몇 가지 지저분한 버그도 수정했습니다.
AdGuard Home 0.107.46


출시일: 2024년 3월 20일
이전 릴리스의 노트에서 약속한 대로 이번 버전에서는 몇 가지 버그가 수정되었으며 앱이 개선되었습니다.
AdGuard Home 0.107.45


출시일: 2024년 3월 7일
이 버전에는 보안 업데이트, 버그 수정 및 새로운 기능이 포함되어 있습니다.
AdGuard Home 0.107.44


출시일: 2024년 2월 6일
새 버전에는 새로운 주요 기능이 추가되지는 않았지만, 몇 가지 변경 사항이 적용되고 다양한 버그가 수정되었습니다. 이제 AdGuard Home을 더욱 편리하게 사용할 수 있습니다!
AdGuard Home 0.107.43


출시일: 2023년 12월 11일
Everybody needs something to keep themselves warm during the cold winter days ❄️. Many people opt for hot coffee ☕ or hot chocolate, but we at AdGuard prefer hotfixes 🔥.
AdGuard Home 0.107.42


출시일: 2023년 12월 7일
As the winter holidays approach, many of us begin to think about what gifts we will give and receive 🎁. With AdGuard, the holidays come early: we decided not to wait too long and present you with this new version of AdGuard Home today!
Among the long-awaited features in this release are the option to enable caching for persistent clients with custom DNS upstream configuration and the option to disable plain DNS for better security.
AdGuard Home 0.107.41


출시일: 2023년 11월 13일
이번 버전에서는 몇 가지 버그가 수정되었을 뿐만 아니라 AdGuard Home을 더 쉽게 설정하고 DDoS 공격으로부터 보호할 수 있는 몇 가지 기능이 추가되었습니다!
AdGuard Home 0.107.40


출시일: 2023년 10월 18일
인터넷 사용을 방해하는 버그보다 더 무서운 것이 있을까요? 다행히도 이번 버전에서는 이러한 버그를 수정했습니다.
AdGuard Home 0.107.39


출시일: 2023년 10월 11일
AdGuard Home의 새로운 버전을 만나보세요! 이번 버전에서는 몇 가지 새로운 기능이 추가되고 버그가 수정되었습니다.
AdGuard Home 0.107.38


출시일: 2023년 9월 11일
새 버전은 과일과 같습니다. 사과가 더 맛있을수록 어딘가에 버그( 벌레)가 있을 가능성이 높습니다. 그런 의미에서 이전 버전은 매우 맛있었고, 이번 핫픽스는 나머지 버그를 수정했습니다.
AdGuard Home 0.107.37


출시일: 2023년 9월 9일
이번 버전에서는 오랫동안 기다려주신 기능이 추가되고 버그가 수정되었습니다.
서비스 차단 일시 중지 일정
이제 사용자는 서비스 차단 필터에 대한 일시 중지를 손쉽게 설정할 수 있습니다. 예를 들어, 하루 종일 소셜 네트워크가 차단되지만 퇴근 후 30분 동안은 허용되도록 설정할 수 있습니다.
이 기능은 몇 달 동안 내부 개발 중이었지만, 이번 버전에서는 마침내 웹 UI에서 선보이게 되었습니다.
폴백 서버
오랫동안 기다려주신 또 다른 기능은 메인 업스트림 DNS 서버에 연결할 수 없을 때 사용되는 폴백 서버입니다.
구문은 기본 업스트림 입력과 동일하므로 도메인마다 다른 폴백 서버를 설정할 수 있습니다.
업스트림 통계
DNS 업스트림과 관련된 또 다른 기능은 대시보드에 표시되는 업스트림 통계입니다.
이 기능을 통해 사용자는 어떤 업스트림이 다른 업스트림보다 빠른지, 어떤 업스트림이 가장 많이 사용되고 있는지 확인할 수 있습니다.
감사의 말
오픈 소스 기여자 @ssrahul96을 비롯하여 문제를 제기하고, 번역을 추가하고, 이번 릴리스 테스트에 도움을 주신 모든 분들께 감사드립니다!
AdGuard Home 0.107.36


출시일: 2023년 8월 2일
일부 버그를 수정하고 보안을 강화하기 위해 이 버전을 출시하게 되었습니다. 향후 버전에서 새로운 기능을 추가하기 위해 노력하고 있습니다.
AdGuard Home 0.107.35


출시일: 2023년 7월 26일
In the previous release, we optimized the filtering-rule list updates, achieving up to three times speedup in some cases. However, the new algorithm proved to be too strict, so in this release we have relaxed its validations while maintaining the optimization for more typical filtering-rule lists 🏎️
As always, there are other minor bug fixes in this release as well.
AdGuard Home 0.107.34


출시일: 2023년 7월 12일
이번 릴리스에서는 AdGuard Home의 보안이 개선되고 몇 가지 큰 문제가 수정되었습니다.
세이프 브라우징 및 CPU 사용량 급증
지난 6월에 몇 가지 버그를 수정한 AdGuard Home 보안 업데이트를 출시했지만, 이 업데이트로 인해 또 다른 버그가 발생했습니다. 그 이후로 세이프 브라우징 및 자녀 보호 기능이 제대로 작동하지 않아 성능 저하, 무작위 충돌, CPU 사용량 급증으로 이어질 수 있었습니다.
이 문제를 해결하는 데 한 달이 걸렸고, 커뮤니티 회원들이 아니었다면 훨씬 더 오래 걸렸을 것입니다. 도움을 주신 모든 분들께 진심으로 감사드리며, 특히 @bigwookie와 @TheCableGuy99에게 깊은 감사를 드립니다. 결과적으로 이 버그는 사실 세 가지의 작은 버그였으며, 모두 이번 업데이트에서 수정되었습니다.
Docker HEALTHCHECK
특히 Podman 및 기타 인기 있는 Docker 도구와 함께 사용할 때 많은 문제를 일으켰기 때문에 Docker
HEALTHCHECK 메커니즘이 제거되었습니다.감사의 말
오픈 소스 기여자 @Jiraiya8을 비롯하여 문제를 제기하고 검사하고 번역을 추가하고 이번 버전 테스트에 도움을 주신 모든 분들께 특별히 감사드립니다!
AdGuard Home 0.107.33


출시일: 2023년 7월 3일
이번 버전에서는 몇 가지 버그가 수정되었습니다 🔧. 그 외에도 향후 버전에서 새로운 기능을 더 쉽게 추가할 수 있도록 앱을 개선했습니다.
AdGuard Home 0.107.32


출시일: 2023년 6월 13일
이전 버전의 주요 문제를 수정하는 핫픽스입니다.
AdGuard Home 0.107.31


출시일: 2023년 6월 8일
이전 버전의 두 가지 주요 문제를 수정하는 핫픽스입니다.
AdGuard Home 0.107.30


출시일: 2023년 6월 7일
일부 버그를 수정하고 보안을 강화하기 위해 이 버전을 출시하게 되었습니다. 향후 버전에서 새로운 기능을 추가하기 위해 노력하고 있습니다.
AdGuard Home 0.107.29


출시일: 2023년 4월 18일
이전 버전은 국제 인류 우주 비행의 날에 출시되었지만 AdGuard 로켓이 이륙할 때 몇 가지 작은 문제가 있었습니다. 이번 버전에서는 몇 가지 성가신 버그를 수정하고 클라이언트 무시 기능을 개선했습니다.
AdGuard Home 0.107.28


출시일: 2023년 4월 12일
드디어 새로운 기능이 대거 추가된 새 버전이 출시되었습니다. 이러한 기능 중 여러분이 기다려온 몇 가지 변경 사항을 소개해드리고자 합니다.
글로벌 보호 일시 중지
이제 30초에서 하루 종일까지 설정한 시간 동안 보호를 일시 중지할 수 있습니다. 이 기능은 실수로 차단된 사이트에 접속해야 할 때 또는 AdGuard Home을 완전히 끄지 않고 일시적으로 비활성화하고자 할 때 유용합니다.
 일시 중지 시간이 끝나면 AdGuard Home이 보호 기능을 다시 켭니다.
일시 중지 시간이 끝나면 AdGuard Home이 보호 기능을 다시 켭니다.
 일시 중지 시간이 끝나면 AdGuard Home이 보호 기능을 다시 켭니다.
일시 중지 시간이 끝나면 AdGuard Home이 보호 기능을 다시 켭니다.향상된 세이프서치 제어 기능
Google, Bing, YouTube 등 특정 서비스에 대해 세이프서치 설정을 활성화 또는 비활성화하여 세부적으로 조정할 수 있습니다.
 클라이언트별로도 동일하게 설정할 수 있습니다. 세이프서치의 또 다른 사소한 개선 사항은 IPv6 주소에 대한 더 나은 지원입니다.
클라이언트별로도 동일하게 설정할 수 있습니다. 세이프서치의 또 다른 사소한 개선 사항은 IPv6 주소에 대한 더 나은 지원입니다.
 클라이언트별로도 동일하게 설정할 수 있습니다. 세이프서치의 또 다른 사소한 개선 사항은 IPv6 주소에 대한 더 나은 지원입니다.
클라이언트별로도 동일하게 설정할 수 있습니다. 세이프서치의 또 다른 사소한 개선 사항은 IPv6 주소에 대한 더 나은 지원입니다.
AdGuard Home 0.107.27


출시일: 2023년 4월 5일
이번 버전은 보안 개선 및 버그 수정에 중점을 두고 있습니다. 유일한 변경 사항은 Go 프로그래밍 언어의 버전이 업데이트되었다는 점입니다. 향후 버전에서는 더 많은 변경 사항이 적용될 예정입니다.
AdGuard Home 0.107.26


출시일: 2023년 3월 9일
이번 업데이트에서는 발신 요청을 설정하는 옵션과 요청 유형에 따라 요청을 거부하는 옵션이 추가되었습니다. 또한 수많은 버그가 수정되었습니다.
AdGuard Home 0.107.25


출시일: 2023년 2월 21일
이 핫픽스는 암호화되지 않은 DNS-over-HTTPS를 사용할 때 치명적인 오류를 방지하기 위해 출시되었습니다. 이 오류는 역방향 HTTP 프록시 뒤에 AdGuard Home을 설정한 사용자에게 발생했습니다.
AdGuard Home 0.107.24


출시일: 2023년 2월 16일
AdGuard Home의 새 버전에서는 쿼리 로그 및 통계 화면에서 특정 호스트 이름을 제외하는 방법을 추가했으므로 차단하지 않으려는 호스트 이름을 지정하는 것이 더 편리해졌습니다.
AdGuard Home 0.107.23


출시일: 2023년 2월 1일
새로운 글꼴, 색상 및 버튼! 모두가 사용자 인터페이스 디자인에 대해 논의하는 것을 좋아하지만, 저희는 버그를 수정하고 새로운 기능을 발표하는 것을 훨씬 더 좋아합니다.
이 버전에서는 다크 테마뿐만 아니라 DNS64 표준 지원 및 여러 차단 가능한 서비스가 추가되었습니다. 또한 몇 가지 버그가 수정되었습니다.
AdGuard Home 0.107.22


출시일: 2023년 1월 19일
밝은 인터페이스를 사용하시면 어두운 밤에 밝은 화면을 보는 것은 불편할 수 있습니다. 🔦 AdGuard Home의 새 버전에서는 마침내 다크 테마를 사용할 수 있습니다!
현재 새로운 다크 테마는 아직 실험 단계입니다. 어떤 결함이 발견되면 문제 #5375의 지침에 따라 보고해 주십시오.
AdGuard Home 0.107.21


출시일: 2022년 12월 24일
추운 겨울을 따뜻하게 만들어 줄 핫픽스입니다.
AdGuard Home 0.107.20


출시일: 2022년 12월 7일
월드컵에서 축구 골키퍼가 골을 막기 위해 최선을 다하는 동안 우리는 사용자를 안전하게 보호하고 최신 보안 업데이트를 받기 위해 최선을 다하고 있습니다. 🛡️또한 DNS 캐시를 손쉽게 지울 수 있는 버튼도 추가했습니다.
AdGuard Home 0.107.19


출시일: 2022년 11월 23일
SNS를 사용하지 않는 것은 거의 불가능하지만 @sandervankasteel의 기여 덕분에 이제 SNS를 사용하지 않는 것이 조금 더 쉬워졌을 것입니다. 이제 AdGuard Home은 가장 인기 있는 몇 가지 Mastodon 인스턴스를 차단할 수 있기 때문입니다.
또한 AdGuard Home을 손쉽게 업데이트할 수 있도록
--update 명령줄을 추가했습니다.
AdGuard Home 0.107.17


출시일: 2022년 11월 2일
Despite this release appearing around Halloween, it shouldn't be spooky at all. The main novelty is that the list of services blockable with a single click is now synchronized with AdGuard DNS to make the user experience more unified across AdGuard services. We've also improved support for HTTP/3 as well as fixed a few annoying bugs.
AdGuard Home 0.107.16


출시일: 2022년 10월 7일
This is a security release. There are no new changes besides the update of the Go programming language version. More substantial changes are to come in the subsequent updates.
Full Changelog
Security
Go version has been updated to prevent the possibility of exploiting the CVE-2022-2879, CVE-2022-2880, and CVE-2022-41715 Go vulnerabilities fixed in Go 1.18.7.
AdGuard Home 0.107.15


출시일: 2022년 10월 3일
Sometimes, even a hotfix needs a hotfix. In the previous release, our mitigations turned out to be too restrictive, preventing some AdGuard Home features from working properly. In this release, we fix this along with a few other bugs.
We have also added experimental support for the HTTP/3 standard in the UI, DNS upstreams, and DNS clients!
Full Changelog
Security
As an additional CSRF protection measure, AdGuard Home now ensures that requests that change its state but have no body (such as POST /control/stats_reset requests) do not have a Content-Type header set on them #4970.
Added
Experimental HTTP/3 Support
See #3955 and the related issues for more details. These features are still experimental and may break or change in the future.
DNS-over-HTTP/3 DNS and web UI client request support. This feature must be explicitly enabled by setting the new property
dns.serve_http3 in the configuration file to true.DNS-over-HTTP upstreams can now upgrade to HTTP/3 if the new configuration file property
dns.use_http3_upstreams is set to true.Upstreams with forced DNS-over-HTTP/3 and no fallback to prior HTTP versions using the h3:// scheme.
Fixed
only application/json is allowed errors in various APIs #4970.
AdGuard Home 0.107.14


출시일: 2022년 9월 29일
This is a security release. Users are encouraged to update AdGuard Home as soon as possible.
Full Changelog
Security
A Cross-Site Request Forgery (CSRF) vulnerability has been discovered. The CVE number is to be assigned. We thank Daniel Elkabes from Mend for reporting this vulnerability to us.
SameSite PolicyThe
SameSite policy on the AdGuard Home session cookies has been upgraded to Lax. Which means that the only cross-site HTTP request for which the browser is allowed to send the session cookie is navigating to the AdGuard Home domain.Users are strongly advised to log out, clear browser cache, and log in again after updating.
Removal Of Plain-Text APIs (BREAKING API CHANGE)
We have implemented several measures to prevent such vulnerabilities in the future, but some of these measures break backwards compatibility for the sake of better protection.
The following APIs, which previously accepted or returned
text/plain data, now accept or return data as JSON. All new formats for the request and response bodies are documented in openapi/openapi.yaml and openapi/CHANGELOG.md.GET /control/i18n/current_language;POST /control/dhcp/find_active_dhcp;POST /control/filtering/set_rules;POST /control/i18n/change_language.Stricter
Content-Type Checks (BREAKING API CHANGE)All JSON APIs now check if the request actually has
Content-Type set to application/json.Other Security Changes
AdGuard Home 0.107.13


출시일: 2022년 9월 14일
In this hotfix release with the “lucky” patch number we have fixed a couple of issues that prevented some DHCP clients from receiving their assigned IP addresses. We've also added the new
dns.ipset_file setting, which should help users who maintain large ipsets, for example to use in firewall or VPN settings.Full Changelog
Added
The new optional
dns.ipset_file property, which can be set in the configuration file. It allows loading the ipset list from a file, just like dns.upstream_dns_file does for upstream servers #4686.Changed
The minimum DHCP message size is reassigned back to BOOTP's constraint of 300 bytes #4904.
Fixed
Panic when adding a static lease within the disabled DHCP server #4722.
AdGuard Home 0.107.12


출시일: 2022년 9월 7일
What better way is there to celebrate the coming of autumn than a patch release? In this new version, we have extended and significantly improved AdGuard Home's built-in DHCP server (fixing many bugs in the process) as well as improved our service blocking feature, thanks to many contributions from the community. As always, we have also updated our tooling to make sure that we use the latest versions without any known security issues.
Full Changelog
Security
Go version was updated to prevent the possibility of exploiting the CVE-2022-27664 and CVE-2022-32190 Go vulnerabilities fixed in Go 1.18.6.
Added
New
del DHCP option which removes the corresponding option from server's response #4337. See also a Wiki page.NOTE: This modifier affects all the parameters in the response and not only the requested ones.
A new HTTP API,
GET /control/blocked_services/services, that lists all available blocked services #4535.Changed
The DHCP options handling is now closer to the [RFC 2131][rfc-2131] (#4705).
When the DHCP server is enabled, queries for domain names under
dhcp.local_domain_name not pointing to real DHCP client hostnames are now processed by filters (#4865).The internal DNS client, used to resolve hostnames of external clients and also during automatic updates, now respects the upstream mode settings for the main DNS client #4403.
Deprecated
Ports 784 and 8853 for DNS-over-QUIC in Docker images. Users who still serve DoQ on these ports are encouraged to move to the standard port 853. These ports will be removed from the
EXPOSE section of our Dockerfile in a future release.Go 1.18 support. Future versions will require at least Go 1.19 to build.
Fixed
Dynamic leases created with empty hostnames #4745.
Unnecessary logging of non-critical statistics errors #4850.
AdGuard Home 0.107.11


출시일: 2022년 8월 19일
This hot summer is approaching its end, but hotfixes are still coming in! In this release, we have fixed configuration file migrations not working for people with AdGuard Home versions older than v0.107.7, as well as made a few minor improvements.
--
Full Changelog
--
Added
AdGuard Home 0.107.10


출시일: 2022년 8월 17일
In this new release, we add support for the new Discovery of Designated Resolvers DDR feature, which allows clients using plain DNS to automatically switch to secure protocols. As well as an Arabic localization and fixes for a couple of rather annoying bugs.
Full Changelog
Added
AdGuard Home 0.107.9


출시일: 2022년 8월 3일
Although not a lot of time has passed since the last release, this new one contains a security update, a new feature, a new platform, and some minor fixes :wrench:. It's always nice to have those!
Full Changelog
Security
Go version was updated to prevent the possibility of exploiting the CVE-2022-32189 Go vulnerability fixed in Go 1.18.5. Go 1.17 support has also been removed, as it has reached end of life and will not receive security updates.
Added
Domain-specific upstream servers test. If such test fails, a warning message is shown #4517.
windows/arm64 support #3057.
Changed
UI and update links have been changed to make them more resistant to DNS blocking.
Fixed
Go 1.17 support, as it has reached end of life.
AdGuard Home 0.107.8


출시일: 2022년 7월 19일
버그는 더운 여름날 갑자기 내리는 비처럼 발생할 수 있습니다. 날씨에 영향을 줄 수는 없지만 버그는 수정할 수 있습니다! 이 릴리스의 수정 사항은 다음과 같습니다.
전체 변경 로그
보안
Go 버전은
CVE-2022-1705, CVE-2022-32148, CVE-2022-30631 및 Go 1.17.12에서 수정된 기타 Go 취약점을 악용할 가능성을 방지하기 위해 업데이트되었습니다.수정 사항
AdGuard Home 0.107.7


출시일: 2022년 7월 19일
AdGuard Home의 새로운 버전을 만나보세요!
DNS-over-QUIC: RFC 9250
오랫동안 기다려온 DNS-over-QUIC 프로토콜은 드디어 초안에서 실제 표준인 RFC 9250으로 발전했습니다. 이 릴리스에서는 하위 호환 방식으로 표준의 최종 버전에 대한 지원을 추가합니다.
업스트림에 대한 더 많은 제어
이제 도메인 자체를 제외하면서 도메인의 모든 하위 도메인에 대해 업스트림을 지정할 수 있습니다. 예를 들어 'server-1.example.com'에 대한 쿼리를 DNS 서버 '1.1.1.1'에서 확인하고
example.com은 기본 업스트림(이 예에서는 '94.140 .14.14`)으로 해결되도록 남겨두고 다음을 사용하세요.94.140.14.14
[/*.example.com/]1.1.1.1이제 일반 DNS 업스트림의 정확한 IP 주소를 기억할 필요가 없습니다. 부트스트랩 서버가 이를 해결할 수 있는 한 새로운
udp:// 업스트림 주소 체계를 사용하여 업스트림 주소를 자동으로 확인할 수 있습니다.udp://one.one.one.one # Same as 1.1.1.1.기타 변경 사항
이제 사용자는 런타임 클라이언트 정보를 수집하는 방법을 더 많이 제어할 수 있습니다(이 기능을 비활성화할 수 있음)..
이제 클라이언트 요청의 EDNS 클라이언트 서브넷 정보가 쿼리 로그 페이지에 표시됩니다.
저희는 사용자가 편안하게 서비스를 사용할 수 있도록 도구를 최신 상태로 유지하기 위해 노력합니다.
또한 많은 작은 변경 사항과 수정 사항이 있었습니다. 아래에서 전체 변경 사항을 확인할 수 있습니다.
감사의 말
문제를 제출하고 번역을 추가하고 이 릴리스를 테스트하는 데 도움을 주신 모든 기고자에게 감사드립니다! 그리고 오픈 소스 기여자인 @Lanius-collaris에게 감사드립니다.
전체 변경 로그
보안
CVE-2022-29526, CVE-2022-30634, CVE-2022-30629,
CVE-2022-30580 및 [CVE-2022-29804]https://www.cvedetails.com/cve/CVE-2022-29804) 취약점을 악용할 가능성을 방지하기 위해 Go 버전이 업데이트되었습니다.
CVE-2022-30580 및 [CVE-2022-29804]https://www.cvedetails.com/cve/CVE-2022-29804) 취약점을 악용할 가능성을 방지하기 위해 Go 버전이 업데이트되었습니다.
비밀번호 강도 정책 시행 #3503.
추가된 사항
도메인의 하위 도메인에 대해서만 업스트림 지원 #4503.
clients.runtime_sources 구성 개체를 통해 런타임 클라이언트의 각 소스를 개별적으로 제어하는 기능#3020.구성 파일의 새로운
dns.private_networks 속성을 통해 비공개로 간주되는 네트워크 세트를 사용자 정의하는 기능#3142.쿼리 로그 레코드의 요청 세부 정보 섹션에 있는 EDNS 클라이언트 서브넷 정보
#3978.
udp:// 체계를 사용하는 일반 UDP 업스트림 서버에 대한 호스트 이름 지원
#4166.이제 AdGuard Home이 서비스로 설치될 때 FreeBSD 및 OpenBSD에서 기본적으로 로그가 수집됨 #4213.
변경된 상황
이제 OpenBSD에서 데몬 스크립트는
/bin/sh 쉘 대신 권장 /bin/ksh 쉘을 사용합니다. 이 변경 사항을 적용하려면 데이터를 백업하고 AdGuardHome -s uninstall && AdGuardHome -s install을 실행하세요.역방향 DNS는 이제 런타임 클라이언트에 대한 정보 소스로 가장 가까운 ARP보다 선호됩니다.
보다 탄력적인 ARP 처리를 통해 런타임 클라이언트 감지 기능이 향상되었습니다.
#3597.
낙관적 캐시에서 제공되는 응답의 TTL은 이제 10초로 낮아졌습니다.
도메인별 프라이빗 역방향 DNS 업스트림 서버는 이제 로컬에서 제공되는 네트워크를 가리키는
*.in-addr.arpa 및 *.ip6.arpa 도메인만 허용하도록 검증되었습니다#3381. 참고: 구성에 이미 잘못된 항목이 있는 경우 본질적으로 효과가 없으므로 수동으로 제거하는 것이 좋습니다.응답 필터링은 이제 질문 유형과 반대로 메시지 응답 섹션의 레코드 유형을 사용하여 수행됩니다.
#4238.
빌드 시간 정보를 추가하는 대신 빌드 스크립트는 표준화된 환경 변수 [
SOURCE_DATE_EPOCH][repr]를 사용하여 바이너리가 빌드된 커밋 날짜를 추가합니다#4221. 이것은 패키지 관리자와 자신의 AdGuard 홈을 컴파일하는 사람들을 위해 재현 가능한 빌드를 단순화해야 합니다.구성 파일의
dns.bogus_nxdomain 속성은 이제 IP 주소와 함께 CIDR 표기법을 지원합니다. #1730.구성 변경
이번 릴리스에서는 스키마 버전이 12에서 14로 변경되었습니다
스키마 버전 13 및 이전 버전에서 실제 영구 클라이언트의 배열이었던 객체
clients는 이제 persistent 및 runtime_sources 속성으로 구성됩니다.# BEFORE:
'clients':
- name: client-name
# …
# AFTER:
'clients':
'persistent':
- name: client-name
# …
'runtime_sources':
whois: true
arp: true
rdns: true
dhcp: true
hosts: trueclients.runtime_sources.rdns 필드의 값은 dns.resolve_clients 속성에서 가져옵니다. 이 변경 사항을 롤백하려면 runtime_sources 속성을 제거하고 persistent의 내용을 clients로, clients.runtime_sources.rdns의 값을 dns.resolve_clients로 이동합니다. 그다음에는 schema_version을 다시 13으로 변경합니다.스키마 버전 12 및 이전 버전에서
dns 객체의 일부였던 local_domain_name 속성은 이제 dhcp 객체의 일부입니다.# BEFORE:
'dns':
# …
'local_domain_name': 'lan'
# AFTER:
'dhcp':
# …
'local_domain_name': 'lan'이 변경 사항을 롤백하려면 속성을 다시
dns 개체로 이동하고 schema_version을 다시 12로 변경합니다.더 이상 사용되지 않음
--no-etc-hosts 옵션은 더 이상 사용되지 않습니다. 그 기능은 이제 clients.runtime_sources.hosts 구성 속성에 의해 제어됩니다. v0.109.0은 플래그를 완전히 제거합니다.수정 상황
AdGuard Home 0.107.6


출시일: 2022년 4월 14일
This is a small security-oriented update. This AdGuard Home version requires Go v1.17 and later to build, because older Go versions receive no further support, including security patches.
Aside from that, we've slightly updated
$dnsrewrite modifier to support the user-defined Discovery of Designated Resolvers (DDR). We are planning on continuing to make more improvements to it in the future updates, see #4463.The rest are minor changes and ever-present bugfixes.
Full Changelog
Security
User-Agent HTTP header removed from outgoing DNS-over-HTTPS requests.Go version was updated to prevent the possibility of exploiting the CVE-2022-24675, CVE-2022-27536, and CVE-2022-28327 vulnerabilities.
Added
Changed
Filtering rules with the dnsrewrite modifier that create SVCB or HTTPS responses should use ech instead of echconfig to conform with the latest drafts.
Deprecated
SVCB/HTTPS parameter name
echconfig in filtering rules with the dnsrewrite modifier. Use ech instead. v0.109.0 will remove support for the outdated name echconfig.Obsolete --no-mem-optimization option #4437. v0.109.0 will remove the flag completely.
Fixed
I/O timeout errors when checking for the presence of another DHCP server.
Network interfaces being incorrectly labeled as down during installation.
Rules for blocking the QQ service #3717.
Removed
Go 1.16 support, since that branch of the Go compiler has reached end of life and doesn't receive security updates anymore.
AdGuard Home 0.107.5


출시일: 2022년 4월 14일
This is a security release. There are no new changes besides the update of the Go programming language version.
More substantial changes are to come in the subsequent updates.
Full Changelog
Security
Go version was updated to prevent the possibility of exploiting the CVE-2022-24921 vulnerability. As the CVE page is still showing “reserved” at the time of publishing, see also golang/go#51112.
AdGuard Home 0.107.4


출시일: 2022년 4월 14일
A small update to fix a couple bugs and shore up some Go vulnerabilities.
More substantial changes are to come in the subsequent updates.
Full Changelog
Security
Go version was updated to prevent the possibility of exploiting the CVE-2022-23806, CVE-2022-23772, and CVE-2022-23773 vulnerabilities.
Changed
Minor UI improvements.
Fixed
AdGuard Home 0.107.3


출시일: 2022년 2월 3일
This version contains bug fixes and cleanups 🧹. Also, there is a new minor feature: now you can rewrite responses for domains using the response code
NOERROR. Similar rules will allow to get a successful response without records, e.g.:|example.com^$dnsrewrite=NOERRORFull Changelog
Added
AdGuard Home 0.107.2


출시일: 2022년 1월 12일
You know, it is very hard to break your bad habits. We're still struggling with one, the overwhelming need to roll out hotfixes to AdGuard Home releases 😢
Now this one is a hotfix release for a really critical CPU overconsumption bug in v0.107.1.
Please update asap and with this, we wish you happy holidays!🎄
Full Changelog
Fixed
Infinite loops when TCP connections time out (#4042).
AdGuard Home 0.107.1


출시일: 2022년 1월 12일
In a not-futile-at-all-we-swear 😅 attempt to fix all bugs before the New Year we're rolling out a hotfix to the recent v0.107.0. Hopefully, this time we got it all right. And if not, there are still a couple of sheets left on the calendar 📆 and the mug is still half-full with lukewarm coffee ☕
Acknowledgements
A special thanks to our open-source contributors: @Aikatsui and @mdawsonuk, as well as to everyone who filed and inspected issues, added translations, and helped us test this release!
Full Changelog
Changed
The validation error message for duplicated allow- and blocklists in DNS settings now shows the duplicated elements (#3975).
Fixed
ipset initialization bugs (#4027).Legacy DNS rewrites from a wildcard pattern to a subdomain (#4016).
Service not being stopped before running the
uninstall service action (#3868).Broken
reload service action on FreeBSD.Legacy DNS rewrites responding from upstream when a request other than
A or AAAA is received (#4008).Panic on port availability check during installation (#3987).
Incorrect application of rules from the OS's hosts files (#3998).
AdGuard Home 0.107.0


출시일: 2022년 1월 12일
We've had some big AdGuard Home updates in the past, but this one is to top them all. It's been brewing for almost eight months! 🙀 So no wonder there's heaps upon heaps of new features, improvements, bugfixes, and other changes. We'd better start listing them ASAP, or else we'll be risking missing the New Year's fireworks 🎆 🥂
Native Apple Silicon support
There's no shortage of killer features in this changelog, but this one takes the cake as the biggest of them all, without any doubt. You won't have to resort to Rosetta or any such solutions anymore if you want to configure AdGuard Home on a Mac with a Silicon chip.
RFC 9000 support In DNS-over-QUIC
It's not quite over nine thousand, but it'll do. The IETF has formalized QUIC this year with RFC 9000, and DNS-over-QUIC protocol finally supports it. If you haven't tried DoQ yet, consider this a sign.
$dnsrewrite rules and other DNS rewrites will now be applied even when protection is disabled (#1558)
Another popular demand. This change only makes sense, as DNS rewrites often carry a different purpose than simply blocking ads or trackers. You still can disable them by opening the admin panel, going to Settings → General settings, and removing the check mark from the Block domains using filters and hosts files box.
Note: rules contained in system hosts files (e.g.
/etc/hosts) now have higher priority. This may result in more rewrites appearing in your Query log. If some of these rewrites are invalid, remove the corresponding lines from your hosts files or comment them out.DNS-over-HTTPS queries now use the real IP address of the client instead of the address of the proxy (#2799)
Note that this change concerns only those proxies that you've added to the list of "Trusted proxies", otherwise it would be a major security risk. We wouldn't want anything of that sort to happen to you! 🙅♀️ Right now
trusted_proxies can only be configured in AdGuardHome.yaml, but that might change in the future.Optimistic DNS cache (#2145)
To reduce latency you may make AdGuard Home respond from the cache even when the stored entry is expired, while trying to refresh them at the same time🔄 This checkbox is located in Settings → DNS settings → DNS cache configuration and it's not ticked by default. Responses made from DNS cache are marked with a special label in the Query log.
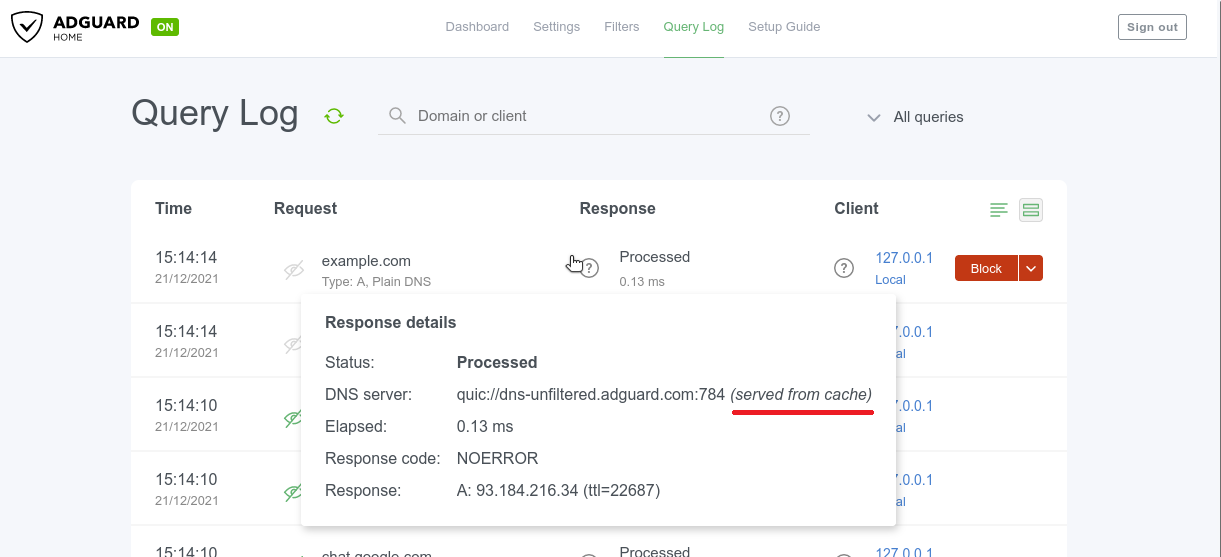
Query log search now supports internationalized domains (#3012)
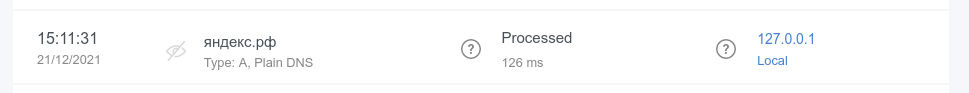
Internationalized domain names (IDNAs) are domain names that contain symbols in non-Latin script/alphabet, such as
яндекс.рф or ουτοπία.δπθ.gr, for example. Previously, they were being converted to Unicode in AG Home Query log (xn--d1abqjx3f.xn--p1ai and xn--kxae4bafwg.xn--pxaix.gr in our examples), which is a detriment in most cases. Now IDNAs are displayed as is, and you can search for them without resorting to Unicode.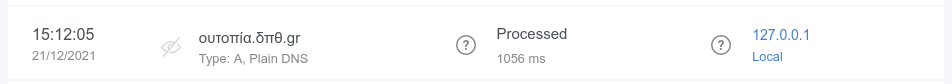
Acknowledgements
A special thanks to our open-source contributors: @Aikatsui, @anbraten, @bruvv, @DandelionSprout, @fvdm, @hnefatl, @markhicken, @p27877, and @systemcrash, as well as to everyone who filed and inspected issues, added translations, and helped us test this release! 🙏
Full Changelog
Added
Upstream server information for responses from cache (#3772). Note that old log entries concerning cached responses won't include that information.
Finnish and Ukrainian translations.
Setting the timeout for IP address pinging in the "Fastest IP address" mode through the new
fastest_timeout field in the configuration file (#1992).Static IP address detection on FreeBSD (#3289).
Optimistic cache (#2145).
New possible value of
6h for querylog_interval setting (#2504).Blocking access using client IDs (#2624, #3162).
source directives support in /etc/network/interfaces on Linux (#3257).RFC 9000 support in DNS-over-QUIC.
Completely disabling statistics by setting the statistics interval to zero (#2141).
The ability to completely purge DHCP leases (#1691).
Settable timeouts for querying the upstream servers (#2280).
Configuration file parameters to change group and user ID on startup on Unix (#2763).
Experimental OpenBSD support for AMD64 and 64-bit ARM CPUs (#2439, #3225, #3226).
Support for custom port in DNS-over-HTTPS profiles for Apple's devices (#3172).
darwin/arm64 support (#2443).freebsd/arm64 support (#2441).Output of the default addresses of the upstreams used for resolving PTRs for private addresses (#3136).
Detection and handling of recurrent PTR requests for locally-served addresses (#3185).
The ability to completely disable reverse DNS resolving of IPs from locally-served networks (#3184).
New flag
--local-frontend to serve dynamically changeable frontend files
from disk as opposed to the ones that were compiled into the binary.Changed
Port bindings are now checked for uniqueness (#3835).
The DNSSEC check now simply checks against the AD flag in the response (#3904).
Client objects in the configuration file are now sorted (#3933).
Responses from cache are now labeled (#3772).
Better error message for ED25519 private keys, which are not widely supported (#3737).
Cache now follows RFC more closely for negative answers (#3707).
$dnsrewrite rules and other DNS rewrites will now be applied even when the protection is disabled (#1558).DHCP gateway address, subnet mask, IP address range, and leases validations (#3529).
The
systemd service script will now create the /var/log directory when it doesn't exist (#3579).Items in allowed clients, disallowed clients, and blocked hosts lists are now required to be unique (#3419).
The TLS private key previously saved as a string isn't shown in API responses anymore (#1898).
Better OpenWrt detection (#3435).
DNS-over-HTTPS queries that come from HTTP proxies in the
trusted_proxies list now use the real IP address of the client instead of the address of the proxy (#2799).Clients who are blocked by access settings now receive a
REFUSED response when a protocol other than DNS-over-UDP and DNSCrypt is used.querylog_interval setting is now formatted in hours.Query log search now supports internationalized domains (#3012).
Internationalized domains are now shown decoded in the query log with the original encoded version shown in request details (#3013).
When /etc/hosts-type rules have several IPs for one host, all IPs are now returned instead of only the first one (#1381).
The setting
rlimit_nofile is now in the os block of the configuration file, together with the new group and user settings (#2763).Permissions on filter files are now
0o644 instead of 0o600 (#3198).Configuration Changes
In this release, the schema version has changed from
10 to 12.Parameter
dns.querylog_interval, which in schema versions 11 and earlier used to be an integer number of days, is now a string with a human-readable duration:# BEFORE:
'dns':
# …
'querylog_interval': 90
# AFTER:
'dns':
# …
'querylog_interval': '2160h'To rollback this change, convert the parameter back into days and change the
schema_version back to 11.Parameter
rlimit_nofile, which in schema versions 10 and earlier used to be on the top level, is now moved to the new os object:# BEFORE:
'rlimit_nofile': 42
# AFTER:
'os':
'group': ''
'rlimit_nofile': 42
'user': ''To rollback this change, move the parameter on the top level and change the
schema_version back to 10.Deprecated
Go 1.16 support. v0.108.0 will require at least Go 1.17 to build.
Fixed
EDNS0 TCP keepalive option handling (#3778).
Rules with the
$denyallow modifier applying to IP addresses when they shouldn't (#3175).The length of the EDNS0 client subnet option appearing too long for some upstream servers (#3887).
Invalid redirection to the HTTPS web interface after saving enabled encryption settings (#3558).
Incomplete propagation of the client's IP anonymization setting to the statistics (#3890).
Incorrect
$dnsrewrite results for entries from the operating system's hosts file (#3815).Matching against rules with
| at the end of the domain name (#3371).Incorrect assignment of explicitly configured DHCP options (#3744).
Occasional panic during shutdown (#3655).
Addition of IPs into only one as opposed to all matching ipsets on Linux (#3638).
Removal of temporary filter files (#3567).
Panic when an upstream server responds with an empty question section (#3551).
9GAG blocking (#3564).
DHCP now follows RFCs more closely when it comes to response sending and option selection (#3443, #3538).
Occasional panics when reading old statistics databases (#3506).
reload service action on macOS and FreeBSD (#3457).Inaccurate using of service actions in the installation script (#3450).
Client ID checking (#3437).
Discovering other DHCP servers on
darwin and freebsd (#3417).Switching listening address to unspecified one when bound to a single specified IPv4 address on Darwin (macOS) (#2807).
Incomplete HTTP response for static IP address.
DNSCrypt queries weren't appearing in query log (#3372).
Wrong IP address for proxied DNS-over-HTTPS queries (#2799).
Domain name letter case mismatches in DNS rewrites (#3351).
Conflicts between IPv4 and IPv6 DNS rewrites (#3343).
Letter case mismatches in
CNAME filtering (#3335).Occasional breakages on network errors with DNS-over-HTTP upstreams (#3217).
Errors when setting static IP on Linux (#3257).
Treatment of domain names and FQDNs in custom rules with
$dnsrewrite that use the PTR type (#3256).Redundant hostname generating while loading static leases with empty hostname (#3166).
Domain name case in responses (#3194).
Custom upstreams selection for clients with client IDs in DNS-over-TLS and DNS-over-HTTP (#3186).
Incorrect client-based filtering applying logic (#2875).
Removed
Go 1.15 support.
AdGuard Home 0.106.3


출시일: 2021년 5월 19일
More! More bugfixes! 🧟♀️
But this time, for a change, there's a couple of new minor features to go with them. Hope you don't mind 🤷♂️
A special thanks to our open-source contributor, @ashishwt, as well as to everyone who filed and inspected issues, added translations, and helped us to test this release!
Added
Changed
Add microseconds to log output.
Fixed
Intermittent "Warning: ID mismatch" errors #3087.
Error when using installation script on some ARMv7 devices #2542.
Local PTR request recursion in Docker containers #3064.
Ignoring client-specific filtering settings when filtering is disabled in general settings #2875.
Disallowed domains are now case-insensitive #3115.
Other minor fixes and improvements.
AdGuard Home 0.106.2


출시일: 2021년 5월 19일
It's not Friday? Not a problem! We defy the tradition of Friday hotfixes by rushing another one out a day earlier 🙌
A special thanks to our open-source contributor, @jankais3r, as well as to everyone who filed issues, added translations, and helped us to test this release!
Fixed
AdGuard Home 0.106.1


출시일: 2021년 5월 19일
We had a release a couple days ago. You all knew it would come to this. 🦸
It's Friday.
It's hotfix time! 🔥
Nothing serious though, we didn't even break anything. Just cleaning up some minor bugs. 🧹
Fixed
AdGuard Home 0.106.0


출시일: 2021년 5월 19일
Quite a lot of changes this time around, even if there aren't as many standouts as in some of the previous updates. We're sure that you'll be able to find a line or two in the changelog that speaks to you!
And one of the reasons for that is the constant support from the community. 👥👥 Special thanks to our open-source contributors: @jvoisin and @Paraphraser, as well as to everyone who filed issues, added translations, and helped us to test this release! 🙇
The ability to set up custom upstreams to resolve PTR queries for local addresses and to disable the automatic resolving of clients' addresses #2704
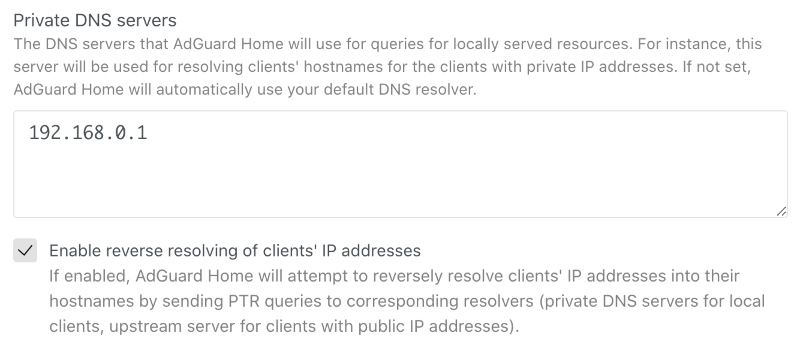
This option will improve your DNS privacy when it comes to addressing local resources. Give it a go unless you want to share your private data with googles of the world.
Search by clients' names in the query log #1273
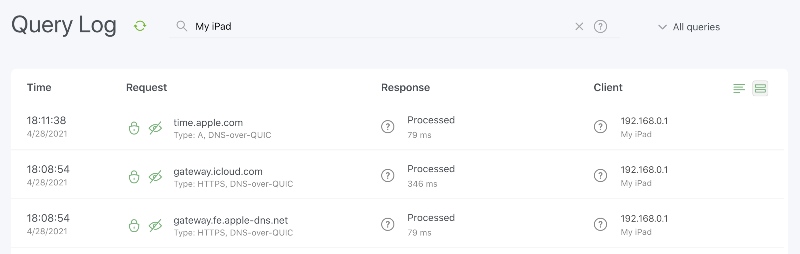
There's not much that can be said about this feature, it's quite self-explanatory: now you can search up queries by specific clients. 🤷♀️
However, we wanted to highlight it anyway since so many of you have asked for it for quite a while. Hopefully, we delivered! 😅
Added
The ability to block user for login after configurable number of unsuccessful attempts for configurable time #2826.
$denyallow modifier for filters #2923.Hostname uniqueness validation in the DHCP server #2952.
Hostname generating for DHCP clients which don't provide their own #2723.
New flag
--no-etc-hosts to disable client domain name lookups in the operating system's /etc/hosts files #1947.Logging of the client's IP address after failed login attempts #2824.
Verbose version output with
-v --version#2416.The ability to serve DNS queries on multiple hosts and interfaces #1401.
Changed
Quality of logging #2954.
The access to the private hosts is now forbidden for users from external networks #2889.
The reverse lookup for local addresses is now performed via local resolvers #2704.
Stricter validation of the IP addresses of static leases in the DHCP server with regards to the netmask #2838.
Stricter validation of
$dnsrewrite filter modifier parameters #2498.New, more correct versioning scheme #2412.
Deprecated
Go 1.15 support. v0.107.0 will require at least Go 1.16 to build.
Fixed
Multiple answers for
$dnsrewrite rule matching requests with repeating patterns in it #2981.Root server resolving when custom upstreams for hosts are specified #2994.
Inconsistent resolving of DHCP clients when the DHCP server is disabled #2934.
Comment handling in clients' custom upstreams #2947.
Overwriting of DHCPv4 options when using the HTTP API #2927.
Assumption that MAC addresses always have the length of 6 octets #2828.
Support for more than one
/24 subnet in DHCP #2541.Invalid filenames in the
mobileconfig API responses #2835.Removed
Go 1.14 support.
AdGuard Home 0.105.2


출시일: 2021년 3월 15일
There are big flashy updates, and there are seemingly unassuming ones, which constitute, however, the backbone of any successful project. This is the latter, as you may have guessed. You'll find here a heap of bugfixes and a security update for CVE-2021-27935.
Security
Session token doesn't contain user's information anymore (#2470).
Fixed
Incomplete hostnames with trailing zero-bytes handling (#2582).
Wrong DNS-over-TLS ALPN configuration (#2681).
Inconsistent responses for messages with EDNS0 and AD when DNS caching is
enabled (#2600).
Incomplete OpenWrt detection (#2757).
DHCP lease's
expired field incorrect time format (#2692).Incomplete DNS upstreams validation (#2674).
Wrong parsing of DHCP options of the
ip type (#2688).
AdGuard Home v0.105.1


출시일: 2021년 2월 16일
Have you ever thought about why traditions are so important?🧙♂️ Traditions help us remember that we are part of a history that defines our past, shapes who we are today, and who we are likely to become. This is why we at AdGuard respect our traditions, and the most important one is pushing the inevitable hotfix right after every major update.🔥🔧
Jokes aside, here's the list of things fixed and improved in this hotfix.
Changed
"Permission denied" errors when checking if the machine has a static IP no
longer prevent the DHCP server from starting (#2667).
The server name sent by clients of TLS APIs is not only checked when
strict_sni_check is enabled (#2664).Fixed
Error when enabling the DHCP server when AdGuard Home couldn't determine if
the machine has a static IP.
Optical issue on custom rules (#2641).
Occasional crashes during startup.
The field
"range_start" in the GET /control/dhcp/status HTTP API response
is now correctly named again (#2678).DHCPv6 server's
ra_slaac_only and ra_allow_slaac settings aren't reset to
false on update any more (#2653).The
Vary header is now added along with Access-Control-Allow-Origin to
prevent cache-related and other issues in browsers (#2658).The request body size limit is now set for HTTPS requests as well.
Incorrect version tag in the Docker release (#2663).
DNSCrypt queries weren't marked as such in logs (#2662).
AdGuard Home 0.105.0


출시일: 2021년 2월 12일
We took our sweet time with this update, but you'll most certainly find it to be worth the wait. The changelog contains three absolute 💥bangers and a laundry list of lesser changes.
🕵️♂️ Client ID support for DNS-over-HTTPS, DNS-over-QUIC, and DNS-over-TLS #1387
This feature would be really useful to those of you who run an encrypted DNS resolver on a public server. In short, you can now identify your devices not just by their IP address (which is, frankly, not too useful in a public server scenario 🤷♀️), but by using a special "Client ID".

Here's how it works:
First, you add a client and specify an arbitrary string as its "Identifier", for instance,
my-iphone.On the client device you can now configure:
DNS-over-HTTPS: https://example.org/dns-query/my-iphoneQueries and stats are now properly attributed to your device.

🔐 AdGuard as a DNSCrypt-resolver #1361
DNSCrypt was the very first DNS encryption protocol that got some traction. It may not be as popular as DoH/DoT/DoQ now, but it is still viable. Moreover, performance-wise DNSCrypt is better than any of them. And now that v0.105.0 is out, AdGuard Home can be configured to work as a DNSCrypt resolver!
However, here goes the tricky part. We haven't yet exposed these settings to the Web admin panel so if you want to have DNSCrypt, you'll need to follow this instruction and do it via editing the configuration file (
AdGuardHome.yaml). Not that it would scare you off, would it? 🤓
Regarding DNSCrypt clients - AdGuard for Android, Windows and iOS support it, Mac will get its support pretty soon. Besides that, here is a long list of client software that supports it as well.
🆎 $dnsrewrite and $dnstype modifiers #2102#2337
AdGuard Home now supports two more powerful rule modifiers that will help blocklists' maintainers.
$dnstype lets you narrow down the rule scope and apply it only to queries of a specific type(s). For instance, Apple devices now support HTTPS DNS query type. While being generally a good thing, this new type may sometimes be harmful😲. By using $dnstype you can block it completely using a simple rule like this: $dnstype=HTTPS$dnsrewrite is another powerful modifier that allows you to modify DNS responses. Note that this modifier is much more powerful compared to something like a hosts file.Here are some examples:
||example.org^$dnsrewrite=SERVFAIL;; - return SERVFAIL for example.org and all it's subdomains|test.example.org^$dnsrewrite=NOERROR;TXT;hello_world - add a TXT record for test.example.org|example.org^$dnsrewrite=example.com - redirect example.org to example.com|example.org^$dnsrewrite=1.1.1.1 - redirect example.org to example.comYou can find more examples in the documentation.
Added
The host checking API and the query logs API can now return multiple matched rules #2102
Detecting of network interface configured to have static IP address via
/etc/network/interfaces#2302A 5 second wait period until a DHCP server's network interface gets an IP address #2304
HTTP API request body size limit #2305
Changed
Access-Control-Allow-Origin is now only set to the same origin as the domain, but with an HTTP scheme as opposed to *#2484workDir now supports symlinks.Stopped mounting together the directories
/opt/adguardhome/conf and /opt/adguardhome/work in our Docker images #2589When
dns.bogus_nxdomain option is used, the server will now transform responses if there is at least one bogus address instead of all of them #2394. The new behavior is the same as in dnsmasq.Made the mobileconfig HTTP API more robust and predictable, add parameters and improve error response #2358
Improved HTTP requests handling and timeouts #2343
Our snap package now uses the
core20 image as its base #2306Deprecated
Go 1.14 support. v0.106.0 will require at least Go 1.15 to build.
The
darwin/386 port. It will be removed in v0.106.0.The
"rule" and "filter_id" fields in GET /filtering/check_host and
GET /querylog responses. They will be removed in v0.106.0 #2102Fixed
Autoupdate bug in the Darwin (macOS) version #2630
Inability to set DNS cache TTL limits #2459
Possible freezes on slower machines #2225
A mitigation against records being shown in the wrong order on the query log page #2293
A JSON parsing error in query log #2345
Incorrect detection of the IPv6 address of an interface as well as another infinite loop in the
/dhcp/find_active_dhcp HTTP API #2355Removed
The undocumented ability to use hostnames as any of
bind_host values in the configuration. Documentation requires them to be valid IP addresses, and now the implementation makes sure that that is the case #2508Dockerfile#2276. Replaced with the script scripts/make/build-docker.sh which uses scripts/make/Dockerfile.Support for pre-v0.99.3 format of query logs #2102
AdGuard Home 0.104.3


출시일: 2021년 2월 12일
Bugfixes... 😌 There's something about them that we just can't resist. We always want more! 🧟
When there's nothing more to fix, we just roll out a new major update, introduce some fresh bugs and start all over. It's a circle of life ☯️
Luckily, there are still some to prey upon in v0.104. Have a look at what we've fixed this time:
Fixed
Don't expose the profiler HTTP API #2336
Load query logs from files after loading the ones buffered in memory #2325
Don't show Unnecessary errors in logs when switching between query log files #2324
Don't show
404 Not Found errors on the DHCP settings page on Windows. Show that DHCP is not currently available on that OS instead #2295Fix an infinite loop in the
/dhcp/find_active_dhcp HTTP API method #2301Various internal improvements
AdGuard Home 0.104.1


출시일: 2021년 2월 12일
Those who pay close attention to AdGuard Home releases know that we keep hotfixes close to our hearts 🔥♥️ This time we held for as long as we could, but ultimately gave in to the urge 😔
Here's a patch to v0.104 with some fixes and minor improvements.
Fixed
Solve the
permission denied error when launching a DHCP server on Linux using Snap#2228. Users experiencing this issue should refresh their snap and call:
snap connect adguard-home:network-controlThis won't be required in the future versions.
Use matching fonts in the Custom Filters textarea #2254
Show the correct query type for DNS-over-QUIC queries in query log #2241
Increase the default number of simultaneous requests to improve performance #2257
Always set a secondary DNS in DHCP #1708
Improve stability on DNS proxy restart #2242
Improve logging on DNS proxy restart #2252
Don't show a “Loading” message and don't rerequest logs once we've reached the end of logs on the query log page #2229
Various internal improvements.
AdGuard Home 0.104.0


출시일: 2021년 2월 12일
We have something special for y'all today. Not just an implementation of a new feature but the first ever implementation of a new feature! 😮 This is about DNS-over-QUIC, a new DNS encryption protocol — read on to learn more.
Ah, yes, there's also a bunch of other good stuff, too: DHCP-related changes, a .mobileconfig generator for iOS and macOS, and a handful of other enhancements and bugfixes.
DNS-over-QUIC support #2049
AdGuard Home now natively supports a new DNS encryption protocol called DNS-over-QUIC. DoQ standard is currently in the draft state, and AdGuard Home (and dnsproxy) is it's first open-source implementation.🥇

So what's good about it? 🤔 Unlike DoH and DoT, it uses QUIC as a transport protocol and finally brings DNS back to its roots — working over UDP. It brings all the good things that QUIC has to offer — out-of-the-box encryption, reduced connection times, better performance when data packets are lost. Also, QUIC is supposed to be a transport-level protocol and there are no risks of metadata leaks that could happen with DoH. 🔒
At this moment, the only major public DNS resolver that provides DNS-over-QUIC is AdGuard DNS. 😎 Use
quic://dns-unfiltered.adguard.com in the upstreams settings to start using AdGuard DNS "Non-Filtering".DHCP rework: DHCP6 support, custom DHCP options
We did a huge rework of our DHCP server implementation. Thanks to it, AdGuard Home now supports DHCP6 and allows setting custom DHCP options.
Please note that in order to set DHCP options, you'll need to edit the configuration file.
Add support for DHCPv6: #779
DHCPv6 RA+SLAAC: #2076
DHCP: automatic hostnames: #1956
Add DHCP Options: #1585
iOS and MacOS .mobileconfig generator: #2110
iOS 14 and macOS Big Sur natively support DNS-over-HTTPS and DNS-over-TLS. However, it's not that simple to configure them — you need to install a special "configuration profile" for that. 🤯 In order to make things easier, AdGuard Home can generate these configuration profiles for you. Just head to "Setup Guide" -> "DNS Privacy" and scroll to iOS.
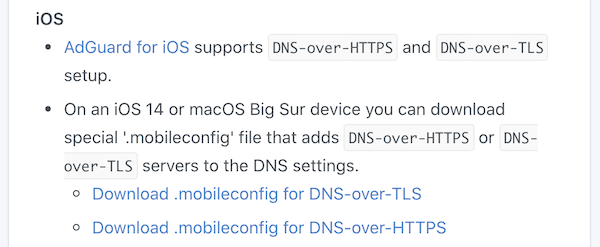
Binary transparency
AdGuard Home binaries are now signed with our GPG key and you can now easily verify that they really come from us: https://github.com/AdguardTeam/AdGuardHome/wiki/Verify-Releases
Other improvements
Allow entering comments to the Upstreams box: #2083
Load upstreams list from a file: #1680
Add ARMv8 to future releases, potentially append a v8 binary to the most recent non-beta release: #2125
Redesign query logs block/unblock buttons: #2050
Treat entries starting with "/" as "://" under specific circumstances: #1950
Use "Null IP" instead of NXDOMAIN by default: #1914
Bootstrap with TCP upstreams: #1843
Add block and unblock buttons to 'check the filtering' result: #1734
ipset feature support: #1191
Add Belarusian and Chinese Traditional HK languages: #2106
Add new language: en-silk: #1796
Use DOH or DOT as bootstrap: #960
Fixed
Reverse lookups return empty answers for hosts from /etc/hosts: #2085
Static lease hostnames are overridden by client-identifier: #2040
Query log doesn't display name for blocked services: #2038
Custom filter editor works with delay: #1657
Incorrect link address: #2209
Smartphone compatible design for user interface: #2152
Misleading information during service installation: #2128
Remove the limit on cache-min-ttl, 3600: #2094
Cannot change minimum TTL override in UI: #2091
Optical Issue on mobile phone: #2090
Setting a large DNS Cache Size in the Web GUI will exceed the unit32 range.: #2056
Clients requests aren't counted properly: #2037
Publish privacy policy on front page (README.md): #1960
Sorting various IP Address Columns in the UI (eg in dhcp static leases) does not sort correctly. They are treated as strings instead of numeric.: #1877
Requests count for clients with CIDR IP addresses: #1824



