Trying hard not to steal your password, they still steal
The analytic software is a greedy monster that devours all the data it can get, no matter how sensitive and private. And no matter if the company owning the software even has a clear plan of making money out of these data. Sometimes they just get trouble instead of profits.
For example, this February, mobile web analytics provider Mixpanel caught itself (and it’s SDK users) collecting user passwords that people typed into forms on sites. Mixpanel soon announced the bug fixed. But, as researchers say, it keeps saving passwords from input fields on some sites even after the patch was released.
It is just not that easy to stop collecting passwords. Developers build their sites and apps in different and not always best ways. They don’t mark password fields in their code in a unique manner. The same feature can be implemented in various manners. Scripts from several different third-party services can interact in an unexpected way. A browser extension can alter page structure making some elements recognizable. There are bugs in app and website code that lead to data vulnerability.
Finally, a function implemented by developers for user comfort and convenience can put them at risk. A "Show Password" option lets users see the password they put in and check it for mistakes. In order to implement this, the user’s password must be placed in a field that doesn’t have its "type" property set to "password", since browsers will automatically mask any text entered into those fields, CITP experts say in their research. Passwords in such fields are not recognized as password and not protected from harvesting.
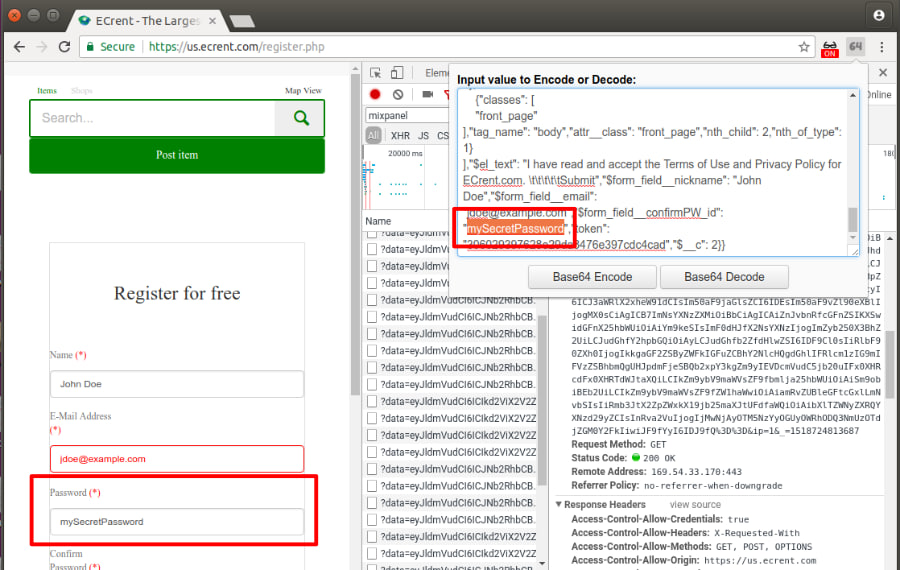
Even if developers don’t implement a "show password", users can install a browser extension that makes passwords visible. Of course, these extensions have the same effect of unmasking passwords for 3rd party scripts.
But the main problem is that analytic systems prefer to gather all the information about user behavior that there is, and filter it afterward, removing the sensitive data. All that is left to users is to trust developers that they would successfully recognize and honestly remove it. Instead of selling to someone or just letting it leak out.
A password is just an example of sensitive data collected by web or mobile analytic software. Another example could be bank card number. Or drugs you take and medical conditions you have. An option called "replay sessions" records and lets replay all the process of user interaction with a site. Including keystrokes and mouse movements.

Analytic scripts just save everything you type and share it generously with dozens of third parties, most of whom just want to sell something to you.
So, what can you do to protect yourself?
- Avoid features like "show password" and others that make visible the sensitive data that your browser hides.
- Do not install browser extensions that make passwords and other hidden input data visible
- Generally, browser extensions are one of the main source or privacy and security threats nowadays. They gather and sell all sorts of data. They contain hidden mining scripts and can distribute malware. They are bought and sold, stolen and hijacked, so a decent extension can suddenly become malicious. It’s better to install only the extensions by big well-known developers and remove the ones you stop using.
- Fill forms attentively. Avoid mistakenly putting sensitive data into fields not meant for it. Credit cars numbers belong only to payment forms, passwords for password fields (and not for sending them by email, for example).
- Use ad blocking and anti-tracking apps
- Use unique passwords, different for every service, so that a leaked password would not be used to steal all your accounts on the Web.




















































