Research says extensions can steal your password from websites. Should you be worried?
Recent research by the University of Wisconsin-Madison found that “a significant percentage” of extensions in Chrome — about 12.5% — have received permissions from users that enable them to access sensitive personal information. The paper mainly focuses on passwords that the researchers say are often stored in plaintext within the source code of even reputable websites. These unprotected passwords, they argue, can become easy targets for malicious data-hungry extensions.
The researchers found that on 15% of the websites they studied — and these are not some obscure and unknown portals, but the likes of Google and Cloudflare (among others) — passwords were “present in plain text in the HTML source code.” In the researchers’ opinion, this careless attitude by website developers combined with relatively lax Chrome rules for extension developers leave the door wide open for attackers to exploit this vulnerability. During their research, they identified 190 extensions that were “directly accessing password fields,” including such popular extensions as AdBlockPlus and Honey — both of them boasting over 10 million downloads.
The researchers said:
“Analyzing the manifest files (the JSON-formatted files that provide important information about the extension’s capabilities and the files it uses), we find that 12.5% (17.3K) extensions have the necessary permissions to extract sensitive information on all web pages.”
While Google Chrome’s new platform for extensions, Manifest V3, has imposed constraints on what extensions can do, the researchers found that these measures did not mitigate risks to security in any substantial way. They said: “Despite MV3’s intended advancements in user privacy and security, content scripts’ operations remain unchanged. This maintains the lack of security boundary between the extension and web page and allows an extension to be loaded on the DOM tree and gain unrestricted access to the webpage, posing security risks for the users.”
Sounds ominous, doesn’t it? So, let’s set things straight.
It’s a trust issue, there’s no getting round it
While it might be true that ad blocking extensions (like many others) require some scary-sounding permissions, it’s not because they are inherently malicious or hell-bent on stealing your data. It’s just they have no other way to do their job. And you have to trust them to do it right.
In fact, it’s by far not the first time that alarm bells have been sounded about the extent to which extensions can access user data. The issue is not specific to Chrome — extensions for other browsers, such as Firefox, have the same capabilities and permissions. Nor is it just about ad blockers: all extensions that need to modify the content of web pages, such as password managers and productivity tools, require broad access to the information on these web pages. The technical reason behind this is that these extensions use JavaScript, a programming language that allows them to read and transform HTML elements on the web page to fulfill their purpose. For example, password managers use JavaScript to insert passwords and usernames into input fields, while productivity tools use it to block distractions, track time, save web pages, etc. So, what about ad blockers?
Ad blockers run JavaScript to scan web pages for ad scripts and other elements that match their blocklist, so that they can block them. It also allows them to hide “ad leftovers” — empty spaces and broken elements that may have been left behind by the blocked ads. This process is called “cosmetic processing.”
In the AdGuard extension description in the Chrome Web Browser Store, we try to be transparent about why we need certain permissions.
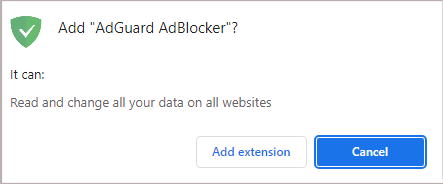
Thus we explain that we need permissions to read and change all your data on all websites (“host permission” in Chrome) and to access tabs (“tabs permission”) in order to block ads, as well as apply cosmetic rules so that web pages look clean and tidy. We also need the webNavigation permission to catch the moment when to inject ad-blocking scriptlets, that is before the page loads any ads.
To sum it up, the AdGuard extension, as well as many others, may require intrusive-sounding permissions to work. Ultimately, it’s up to you if you trust their developers and their justifications for needing these permissions enough to grant them.
So, should you be worried?
Yes, in the grand scheme of things, you should. You should be mindful when installing extensions that can access your data on web pages. Even if rather slim, there’s a chance that the extension you want to install is a malicious one and will steal your password or banking details that are stored in plaintext in a website’s HTML source code. With additional functionality come additional risks, and this applies not only for add-ons, but also for other services and devices: take WiFi-enabled vacuums or modern cars with sensors, for example. So, to cut to the chase, you will have to accept a higher level of risk to your security and privacy when you allow your add-on to work its magic, such as blocking ads. Regardless of whether you think such a trade-off is fair or not, it is just unavoidable.
In 2018, Mozilla devoted an entire blog post to extension permissions, including “scary-sounding ones”, in which it explained why extensions like ad blockers need them for legitimate reasons, but also highlighted the risks of installing them.
However, the Firefox maker noted that such cases, when a malicious developer claims your extension does one thing while it actually does something else, while possible, are still “rare.”
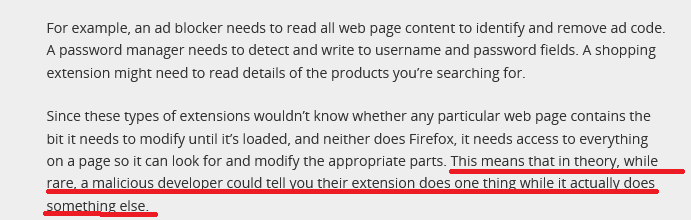
Source: Mozilla
You may argue that even “rare” is sometimes too often. And we agree wholeheartedly — downplaying this problem would do nobody good. A few years ago, we ourselves exposed several malicious ad blocking extensions that ripped off the code of legitimate ones and could change your browser’s behavior in any way. At the time we estimated that over 20,000,000 people could be affected by these fake ad blockers. So now the burning question is, how can you be a little more comfortable giving your extension the ability to see all of your browsing activity?
Well, here’s a checklist that the extension needs to meet to be considered safe in our eyes:
The author of the extension is clearly stated, has a physical address, and, ideally, has been in the industry for many years
The privacy policy is present, clear, and user-friendly
The reasons for permissions are clearly stated, and match the purposes of the extension
The extension is open source: you can see the list of all commits and it’s always available (for example, AdGuard ad blocker extension for Chrome is free and public)
The developer maintains online presence and can be easily contacted by users (via social media, website, or a dedicated support desk) and provides timely responses
The extension has positive ratings and favorable reviews. Although these are not an iron-clad guarantee of it being safe, as reviews can be manipulated by bots or left by non-inquisitive casual users who appreciate the fact that the extension works and don’t look any deeper — but that’s another story





















































