Security experts exposed RoughTed — a massive malvertising operation
Cybersecurity technicians from Malwarebytes.com have researched a malvertising operation that had already been active for about a year with the peak on March, 2017. The malicious ads have gathered about half a billion clicks in just three month.
Malvertising is a cybercrime tool that works by breaking into ad networks and planting infected ads among others. Such adds carry viruses, trojans, ransomware and other types of malware. Notably, such ads needn't to be clicked at — they can do their black work just after being loaded by a browser.
The campaign described by Malwarebytes.com has been called RoughTed. Its ads have the ability to bypass adblockers (including Adblock Plus and uBlock origin). AdGuard users don't need to worry — we have long ago updated our filter lists.
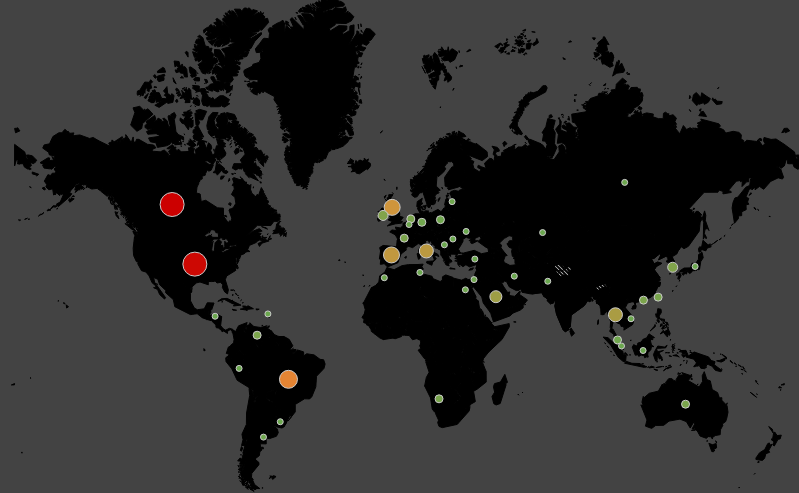
Thanks to Malwarebytes.com, we can now evaluate the entire scale of RoughTed. Ads with malicious code were found on large web properties, many ranked within Alexa's top-1000. The campaign has mostly affected users of the United States and Canada, then - Britain, Italy, Spain and Brazil, but the victims were found in all regions of the world (except China).
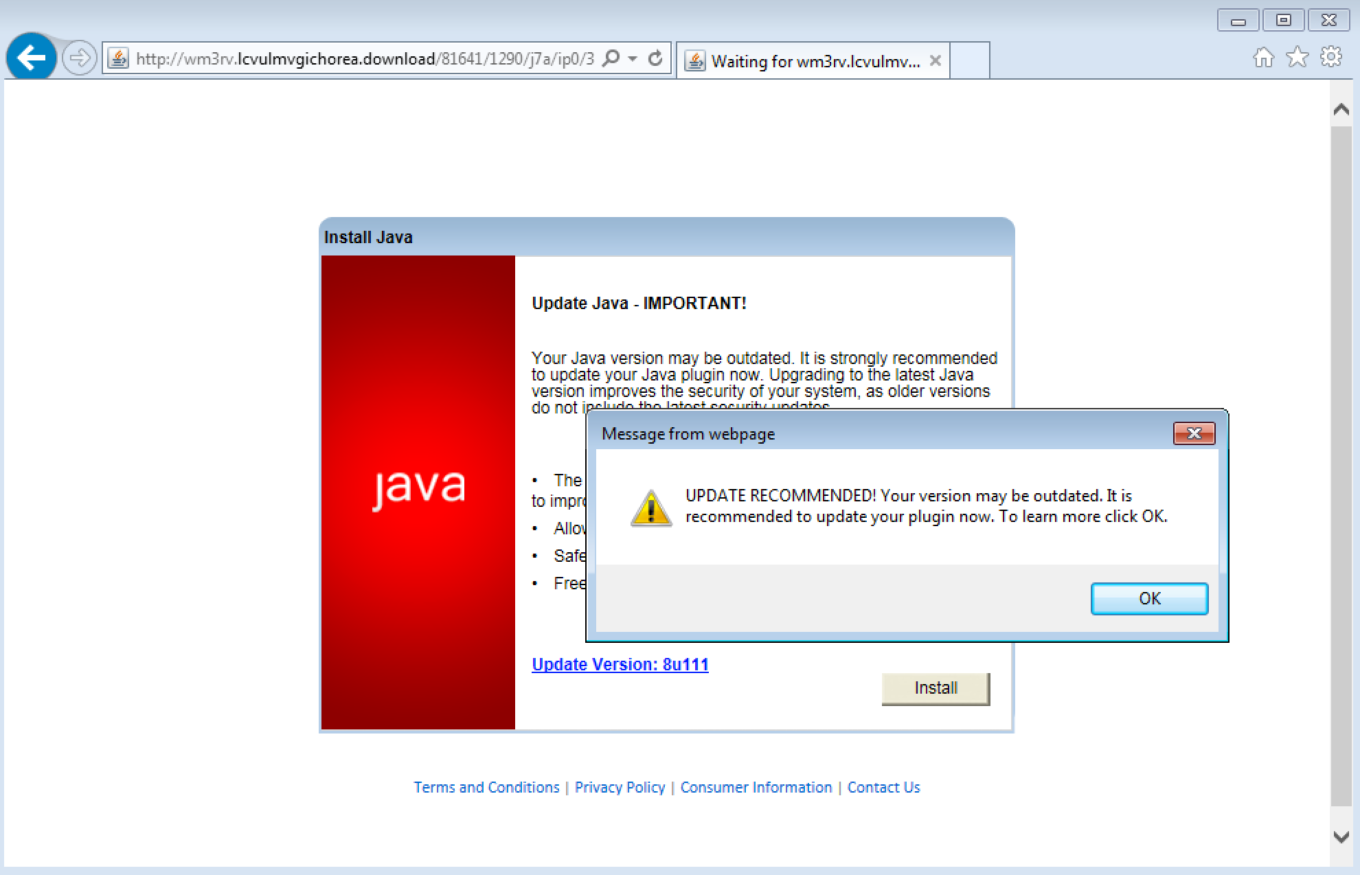
The quality of the RoughTed operation is also impressive. The technologies used for the attacks, just like advertisement targeting software, determined the features of a victim's device - its location, operating system and other data, allowing to choose the optimal method of attack. Someone received a false warning that they need to update the software or contact the support team, someone was treated with a banking trojan (those steal financial information, bank card data, etc.), someone's computers were used to generate app or browser add-on installs (developers pay for app installations)…
Fingerprinting was used for targeting, so it was possible even if the device had programs that block tracking and data mining.
As you can see, the harm from advertising is not limited to its intrusiveness, abuse of time and attention. Accordingly, blocking advertising is not a whim, but a security issue. You should choose a blocker that has agile and competent developers, who keep in touch not only with advertising novelties, but also with cyber threats, and update filters promptly. For example, AdGuard.
Malveritsing has been known for at least 10 years, among the distributors of infected ads were not only porn sites, torrent trackers and small properties whose webmasters were desperate to monetize them with the help of whatever is offered. This role is familiar to the sites of The New York Times (attacked in 2009), Huffington Post, The Daily Mail, Los Angeles Times, Forbes, Yahoo. A previous large malvertising campaign was described in the spring of 2016.
Forbes had a really funny incident: it had been distributing infected ads simultaneously with a campaign against ad blockers. Users with this software didn't see the articles on Forbes.com and saw a call to stop blocking ads. If they did, they became a victim of malware.




















































